Lab: Malware Analysis
Introductory Malware dissection
- Windows
In this lab, you will examine and run live malware called WannaCry.
Overview
If an organization gets hit by malware, upper management all the way to the top will want to know exactly what happened. Basic malware analysis can provide answers for upper management. If you are in a management position, you may want to know answers to questions that approaches in this lab can help answer.
In this lab, you’ll examine the malware WannaCry. This program made international headlines in the summer of 2017 when it wreaked havoc across the world before being disabled by malware analyst Marcus Hutchins, aka MalwareTech.
WannaCry is ransomware that encrypts the victim’s files and demands ransom in order to decrypt. But due to a programming error, WannaCry does not decrypt victim’s files even after the ransom is paid.
Safety considerations
For this lab, you will examine WannaCry within the Windows VM running inside your Kali Linux virtual machine that is not susceptible to WannaCry. Heads up! Therefore, your personal computer will not be at risk of being encrypted by WannaCry as long as you don’t download and run WannaCry on it.
Important: Do not copy WannaCry from the Windows VM to your personal computer. Do everything from Kali and from the Windows VM on Kali.
Below are a list of safety-related questions.
Q: How does WannaCry spread?
This version of WannaCry uses the EternalBlue exploit to spread. Eternal Blue was developed by the NSA, and stolen and leaked by the Shadow Brokers, and subsequently picked up by North Korean agents and used in WannaCry. Microsoft issued a patch for EternalBlue in March 2017.
Q: I run Windows. Am I protected from the WannaCry’s spreader, “EternalBlue”?
Yes, if you have updated your computer since 2017, you are protected from EternalBlue.
Q: I’m patched against EternalBlue. Can I safely run WannaCry directly on my computer?
No. If you manually copy Wannacry to your computer, you have yourself fulfilled the purpose of the EternalBlue spreader.
However, because WannaCry has a built-in killswitch, you still would not be infected as long as you had an internet connection, as you will learn in the lab.
But if you extracted the WannaCry encryptor from the dropper and manually ran it on your computer, you would have bypassed the killswitch. Your files would be encrypted, regardless of your internet connectivity. But it is extremely unlikely that you do this by accident.
Q: Can my personal computer be infected via its remote desktop connection to Kali?
No. Wannacry cannot travel over the remote desktop protocol.
Q: What machines could theoretically be compromised by the EternalBlue spreader running on GCP Kali?
Short answer: Other machines on the same virtual network as the Windows VM, and machines on the public internet, are potentially vulnerable to the EternalBlue spreader when it runs from the Windows VM. But neither of these are a concern for this lab.
Longer answer: It is theoretically possible for WannaCry to spread to other machines if two conditions are met:
- The victim virtual machine has a network adapter that gives it access to other machines on a network,
- The other machines on that network are not patched against WannaCry’s spreading mechanism.
Pay attention! Read the below!
In this lab, you run WannaCry within a virtual machine running on Kali on GCP. The malware has network connectivity to other machines on the network of the compromised host. However, from the perspective of the windows vm running on Kali, the only other devices on the same “network” as the virtual machine are:
- The other kali virtual machines. But these are not vulnerable to WannaCry.
- Other machines on the public internet. But if these are vulnerable to WannaCry, they have already been compromised a billion times over since 2017.
Your personal laptop is not on the same network as the Kali windows virtual machine. The malware cannot jump the Chrome Remote Desktop connection.
Safety tl;dr
As long as you only run the malware on the windows virtual machine running on Kali, you are safe.
Preparation and Recovery
For convenience, take a snapshot of your windows vm before you infect it with wannacry.
virt-manager.If you forget to take a snapshot and you want to undo damage to your virtual machine, you can restore your Windows VM to a pristine state by running the following commands on Kali:
cd /root/vagrant-boxes/lab-windows-2019-vuln
vagrant destroy
vagrant up
Preliminary Analysis
Heads up! Perform all of the following commands from within the Windows VM on Kali.
-
From your Windows VM within Kali, download the worm + loader executable from here.
-
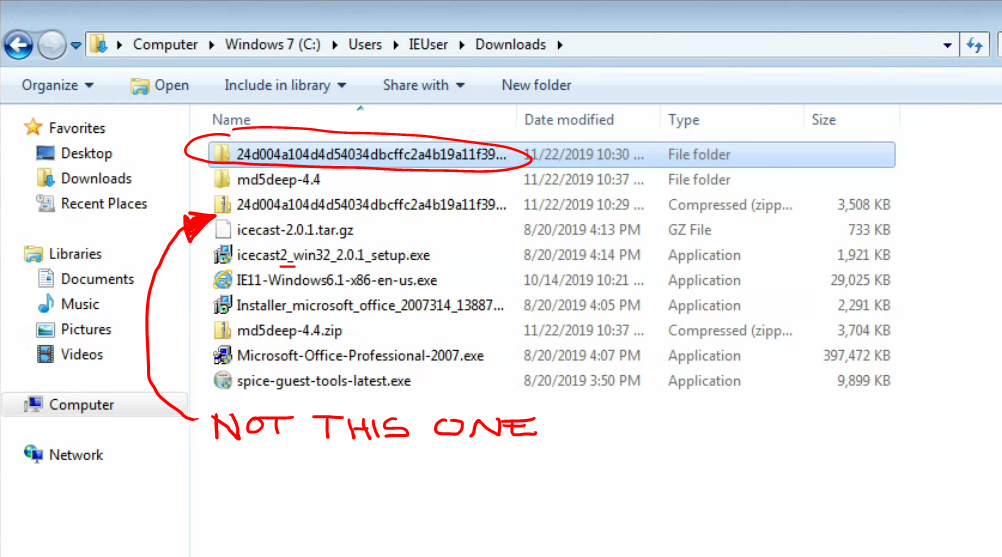
Extract the malware by right-clicking the folder, choosing
Extract all..., and entering the password: “infected”. This will create a new folder called “24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exe.zip”, inside of which is a24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exefile. Do not run this file yet!This is the dropper and spreader only. Technically, it performs no encryption.
-
Dropper:
“[A dropper] is a special type of [malware]. Droppers carry payload to the victim system within itself. Payload is frequently compressed and encrypted or obfuscated. Once executed, a dropper extracts the payload from [itself] and installs it on a victim system (i.e., drops it on the system–which explains the term used for this type of infector). Unlike droppers, downloaders – another type of infector–doesn’t carry payload within itself but rather downloads it from a remote server”
(Rootkits and Bootkits, Matrosov et al. 2019; p. 13).
Wannacry is a dropper – the encryptor is stashed inside of the just-extracted exe. The job of the wannacry dropper is to drop the encryptor on the victim host, and run it.
-
Spreader:
A spreader is a malware component that spreads the malware to other computers on a network. In the case of Wannacry, it scans the network and infects as many other machines as it can. The dropper and spreader are the same file.
-
-
Navigate to the extracted
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exefolder (not the zipped one), and open a cmd prompt in that path by holding down the shift key + right-clicking, then selecting “Open PowerShell window here.”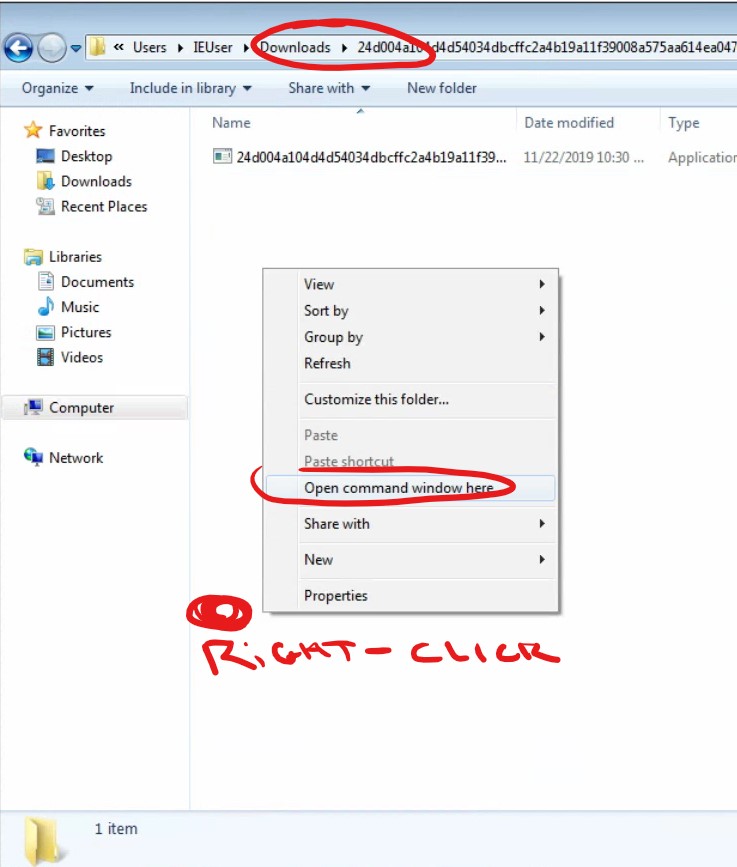
-
Hash the exe using the following commands (use tab-completion for the exe filename).
-
SHA-256 (the default algorithm for the “get-filehash” command):
get-filehash ./24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exe -
MD5:
get-filehash -algorithm MD5 ./24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exe
-
- Using a browser within the Windows VM, search the internet for the hashes to see what comes up. (You can copy them to the clipboard from a cmd prompt by highlighting them and then right-clicking the highlighted text.)
-
Go to https://VirusTotal.com and search for either of the hashes.
VirusTotal can run files and URLs through a barrage of antivirus programs to detect malicious files. This can be much more effective than checking a file against only one or two detection programs. However, people who create viruses also use this site to see whether their malicious code flags, and tweak the code until it comes up clean. It is not uncommon for a piece of malware to only turn up a few hits in VirusTotal.
Question : What does Ad-Aware report this hash to be? -
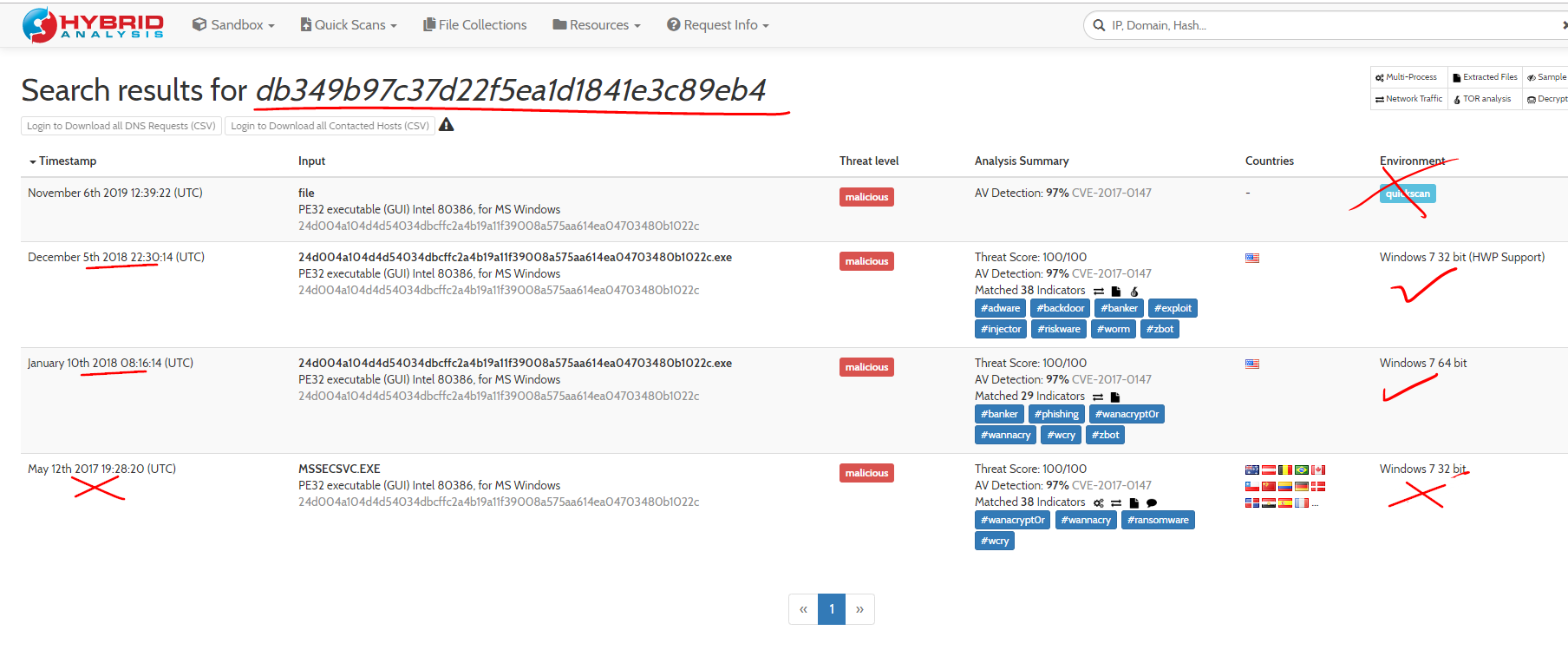
Visit https://hybrid-analysis.com, and search for the hash. Hybrid-analysis will check the hash of the file against previously analyzed files.
Hybrid-Analysis provides “Falcon Reports,” which are analyses of executing malware within certain operating system environments. The search results show a list of reports. The results also show “quickscan” results, which are themselves a collection of sandbox reports for a given sample.
-
Select any of the reports that are from 2018 for one of the “Windows” environments.
-
Note the wide range of information that these reports provide about the executable.
This malware makes a DNS request to one domain name. Examine the domain name that this malware attempts to access – see the “Network Analysis” section (accessible via the menu on the right-hand side), and then the “Contacted Hosts” section. Keep this domain name in mind. The sandbox reports show that the domain name resolved to an IP addresses in the 2018 reports, but not the 2017 one.
Question : What IP address is associated with the domain name that WannaCry attempts to access in the 2018 reports?
-
Now we will manually perform some of the analyses that hybrid-analysis performs, in order to get a hands-on feel for the work involved.
Static Analysis
Static Analysis is usually the first step in malware analysis. It involves gathering as much information as possible from a potential malware file and determining its functionality, purpose, and identifying traits to the greatest degree possible. Static analysis does not involve running the malware file, and thus is less risky than dynamic analysis. However, caution must be used here (and in all stages of analysis), as certain analysis tools may execute the malware without warning.
Using the Strings Program
As its name implies, strings is a command-line tool that will parse through a
file and pull out any character strings in either ASCII or Unicode. The result
of running this tool can tell you many things about potential malware:
- Error messages can give telling information about the functionality of a program.
- IP addresses that the program will call to.
- Windows built-in library function files (DLLs) that the program will try to access.
strings is one of many programs provided by a set of tools originally
developed in 1996 which still rocks called
sysinternals. It is already
installed on your windows virtual machine.
-
From a cmd prompt, confirm that you can run the program
strings:strings -
From a
cmdprompt in the directory where24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exeis located, run the following:strings -n 12 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exe > output.txt -
Then, open output.txt with notepad:
notepad output.txtThe
-noption means “minimum string length.” -
You may recognize this strings output from the hybrid-analysis report.
Tips:
- Use tab-completion to fill out the filename. Do not copy-paste. If you keep copy-pasting, I will turn all code-snippets on the website into screenshots to spite you.
- A convenient shortcut to opening a Windows shell in a certain directory is to use Windows Explorer (the graphical file
explorer thing) to navigate to where you want to go, then
right-click in the white area in that directory listing, then choose “Open PowerShell window here”. PowerShell can do everything a
cmdprompt can do, and more.
-
From notepad, search through output.txt (use
ctrl+f) for an “http://” url. This url is the “killswitch” domain which, when registered, blocked the wannacry spreader from doing its thing. See the comic on this page to understand in four simple comic panels the likely facepalm-reason why that functionality is even in the spreader in the first place.Question : What is the killswitch domain for this worm?
Resource Hacker
Resource Hacker is another useful tool that can often pull information from a malware sample without executing the sample. Windows application development tools will set “resource” values that are stored in the executables. Developers can customize these resource values. Examining these executable resources can sometimes give insight into the malware.
-
Use Chocolately, the Windows package manager, to download and install Resource Hacker. Run the following from a windows
cmdprompt:choco install -y reshack - Open “Resource Hacker” by searching for it from the Windows search bar.
- Load the wannacry worm (
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exe) into resource hacker. -
Navigate through the folder tree structure to see information about the malware.
-
Examine the “Version Info” node, and look at the “FileVersion”. This can be helpful to track to note versions of malware that may be floating around.
Question : What FileVersion does this malware claim to be?Also, look at the CompanyName, FileDescription, and LegalCopyright.
Question : What is the name of the company that this malware claims is its author? -
Applications can embed applications within their resource section, which is accessible via the navbar on the left under the
Rtree. The loader stores the wannacry encryptor here. When the loader runs, if the killswitch is not triggered, it will extract the embedded resource payload, install it, and run it. Let’s extract it manually and play with it.- Expand the “R” node, click on the star range, and then right-click
it. Choose
Save Resources to a BIN file(a BIN file is another name for a.exein Windows). Save it where you like. This is the wannacry encryptor. If you run this, your VM files will be encrypted. - For convenience, rename it to
wannacry-payload.exe.
- Expand the “R” node, click on the star range, and then right-click
it. Choose
-
Strings again, this time on the wannacry encryptor
-
From a cmd prompt in the directory where your newly extracted “wannacry-payload.exe” is located, run the following:
strings -n 12 wannacry-payload.exe > output.txt notepad output.txtRead through the output.txt file and look for sensical strings. Some malware can use “packing” tricks to make it harder for malware analysts to perform static analysis (read more about it here). “Packing” is a form of compressing that is sometimes also combined with encryption. If this malware were “packed”,
stringswould find no sensical text inside. If it is not packed, you will see English words which are names of Windows functions or custom that the malware may call internally.Question : Is this malware likely “packed”, or is it “unpacked”?Consider. If you did not know what this malware did, what would seeing calls in thestringsoutput to Windows functions such as "CryptDecrypt", "CryptEncrypt", "CryptDestroyKey", and "CryptImportKey" tell you? Dadgum right, got ransomware on our dadgum hands.
Analyzing DLLs with Dependency Walker
A few Dynamic Linked Library (dll – the Windows function library) calls appeared when we ran the Strings program above. We can use another program, Dependency Walker, to obtain more information about those dlls and their use by the malware. Dynamic linking is an area that gives a great deal of insight into how a program functions, and it is of particular importance to malware analysis.
-
Use the “choco” windows package manager to install Dependency Walker. From a cmd prompt:
choco install -y dependencywalkerThen, search for and run “Dependency Walker”:
When the program loads, use the “open” button on the top-left and load the wanncry.exe.
-
There’s a lot of information here, so let’s step through it.
- The top-left pane shows all of the DLL files that are called by the WannaCry program.
- The top-right pane shows the functions that are called by the selected DLL.
- The right-middle pane shows all possible functions that could be called by the selected DLL, along with their ordinal values; a function can either be called by its name or by the ordinal value, so if you see an ordinal value called you can use this list to check its functionality. Calling functions by ordinal allows a program to call the function without ever using its name in the code. It can be a useful obfuscation technique.
- The bottom two panes show additional information.
Spend some time looking through the different DLLs.
Question : Under ADVAPI32.DLL, find BCRYPT.DLL. What is function for ordinal value 37, i.e., the 37th function from the top?Bcrypt.dll is a family of functions, documented and listed here. Bcrypt.dll is not the same as the blowcrypt family of algorithms that we studied earlier in the semester. bcrypt.dll lamely refers to "bestcrypt", aka "Cryptography: Next Generation (CNG)" (see here). It is the built-in Windows way to perform encryption. And yes, that means that Wannacry is lamely using Windows functions, instead of making their own functions, to encrypt.
Dynamic Analysis
Now we come to the fun part.
Dynamic Analysis is used to gather information about a file that could not be gathered from static analysis. Dynamic Analysis is inherently riskier than static analysis, as it involves investigating malware as it runs, or the state of the host machine after the malware has executed. The drawbacks of dynamic analysis are that:
- Malware may behave differently in a VM environment if the malware detects that it is in such a setting;
- Malware may behave differently depending on available network and Internet connections, and
- Running malware may potentially expose the host or other hosts on a network to risk, as mentioned previously.
But don’t worry about number 3, you’ll be fine as long as you do all of your work on the Windows VM on Kali.
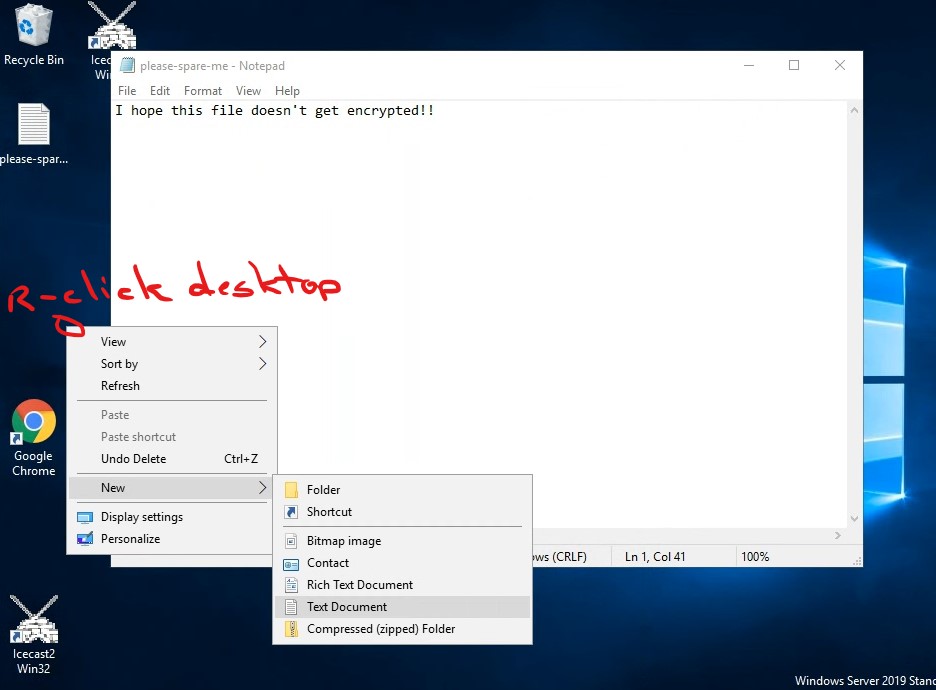
Create a file
Use “notepad” to create a text document with any content, and save it on your Windows VM desktop. This file will be encrypted by wannacry. For example, see the following screenshot:
Process Monitor
You can get basic information from Task Manager in Windows, but Process Monitor allows you to track every action of a given process. Be warned that Process Manager generates a lot of data, all of which it stores in RAM. So, it may quickly fill up the memory of a VM and crash it if left to run for a long time.
No one in their right mind uses Process Monitor without applying some filters. We will apply filters soon to the gigantic pile of data pouring in.
-
Launch Process Monitor by running command
procmonfrom a cmd prompt:procmonWait for Process Monitor to launch.
-
With Process Monitor running, run your 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exe.
OH NO, YOU ARE UNDER ATTACK.
Or are you?
-
Stop Process Monitor from collecting: (
File>Capture Eventsto toggle, or click the button shown below:).
-
From within Process Monitor, launch the Process Tree (
Tools>Process Tree, or click the button shown below):
Examine the Process Tree. Note the entry for
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exe. Highlight it, then clickInclude Process. This will filter the events shown in the main process monitor view to only show associated with our malware worm’s process id (PID).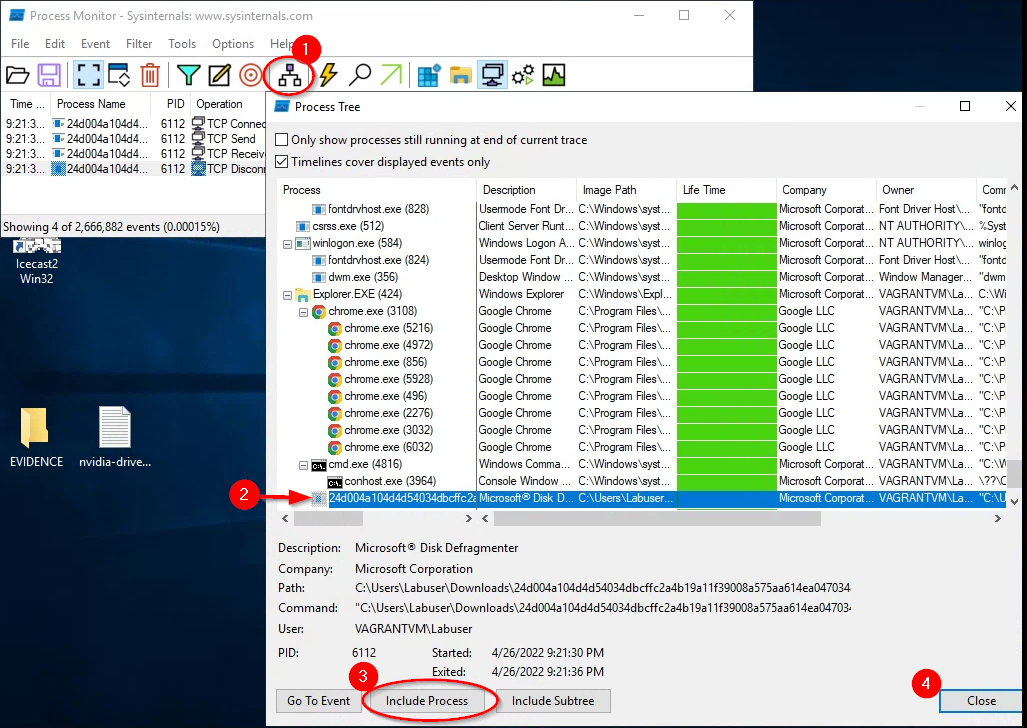
-
In the icon menu on the top of Process Monitor, deselect all icons in the far-right section except for the icon third from the right.
This will filter to show only network calls. This should show at least one
TCP Connectoperation.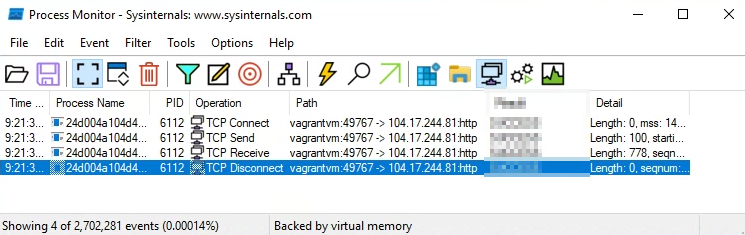
This is the loader calling out to the killswitch domain. If the call resolves successfully, then the malware immediately exits without doing anything else.
Question : What was the value of the “Result” field for any of24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exe’s “TCP Connect” events?
Disable Network Adapters and run the dropper again
The worm can’t resolve the killswitch domain request, and therefore won’t exit, if the virtual machine doesn’t have an internet connection!
Before we proceed, disable both of the VM’s network adapters. To do this, from the VM’s “Details” menu, select both NICs, and for each, change the “Link State” to “inactive.” Once you have successfully done so, the Windows toolbar should show a broken ethernet connection icon. This is desirable.
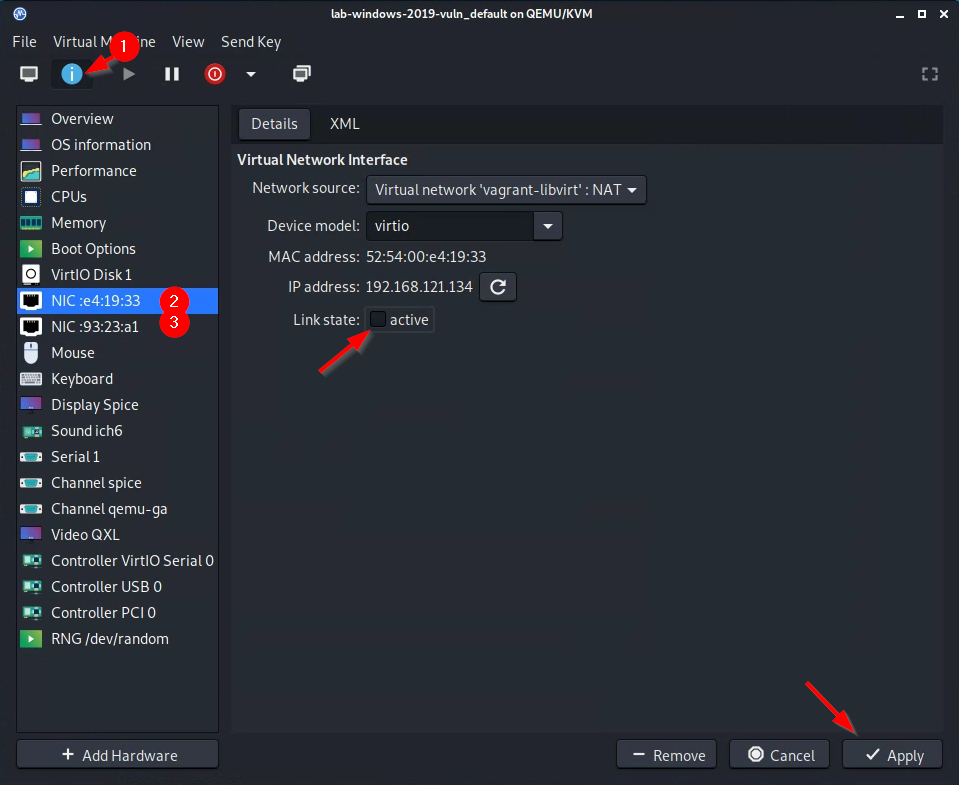
Open Process Monitor again. Do the following from the menu options:
- Filter > Reset Filter
- Edit > Clear display
- File > Capture Events (to enable capturing)
-
With Process Monitor running, right-click
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c.exeand choose “Run as Administrator.”OH NO, YOU ARE UNDER ATTACK. YES, THIS TIME YOU REALLY ARE. TIME TO CRY.
Is running as administrator necesssary? Running as administrator is not strictly necessary for WannaCry to encrypt. But if it is not run as administrator, then in the next step,tasksche.exegets dropped into a random, unpredictable location. -
The dropper installed the file stored in its R resource section into the
C:\Windows\directory, naming ittasksche.exe, and then ran it. This is the wannacry encryptor.Question : What is the sha256 hash ofC:\Windows\tasksche.exe? -
Well, what does this encryptor do?
It scans through the entire drive for files with interesting file extensions, and it encrypts them, storing an encrypted version of the decryption key in header info in the file itself. The encrypted variants of all of your precious files have a
.WNCRYextension.stringsintasksche.exeshows that it is looking for files with the following extensions:.der .pfx .key .crt .csr .p12 .pem .odt .ott .sxw .stw .uot .3ds .max .3dm .ods .ots .sxc .stc .dif .slk .wb2 .odp .otp .sxd .std .uop .odg .otg .sxm .mml .lay .lay6 .asc .sqlite3 .sqlitedb .sql .accdb .mdb .db .dbf .odb .frm .myd .myi .ibd .mdf .ldf .sln .suo .cs .cpp .pas .asm .js .cmd .bat .ps1 .vbs .vb .pl .dip .dch .sch .brd .jsp .php .asp .rb .java .jar .class .sh .mp3 .wav .swf .fla .wmv .mpg .vob .mpeg .asf .avi .mov .mp4 .3gp .mkv .3g2 .flv .wma .mid .m3u .m4u .djvu .svg .ai .psd .nef .tiff .tif .cgm .raw .gif .png .bmp .jpg .jpeg .vcd .iso .backup .zip .rar .7z .gz .tgz .tar .bak .tbk .bz2 .PAQ .ARC .aes .gpg .vmx .vmdk .vdi .sldm .sldx .sti .sxi .602 .hwp .snt .onetoc2 .dwg .pdf .wk1 .wks .123 .rtf .csv .txt .vsdx .vsd .edb .eml .msg .ost .pst .potm .potx .ppam .ppsx .ppsm .pps .pot .pptm .pptx .ppt .xltm .xltx .xlc .xlm .xlt .xlw .xlsb .xlsm .xlsx .xls .dotx .dotm .dot .docm .docb .docx .docIt then pops up an annoying notification about your ransomed state which will continue to pop up every sixty seconds or so. The best way to deal with that popup is not to “X” it out, but rather, to drag it to a corner of your screen, almost out of sight.
Open
notepad, and using its “File” menu, open any of your encrypted files to examine its contents. (To find them, in the dropdown above “Open,” change the filetype filter to “All Files”)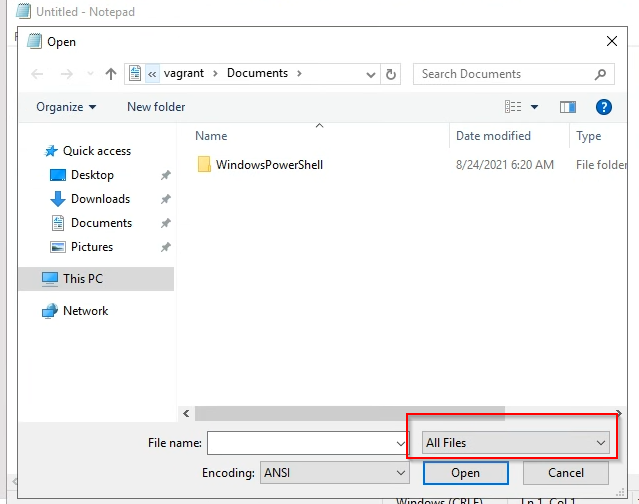
What used to be plaintext now encrypted. The first 8 bytes of any file encrypted by wannacry are always the same. This is wannacry’s “magic number.” It’s readable in ASCII, so you can see it in notepad.
Question : What is the magic number for a wannacry-encrypted file?Note: You can also examine files’ magic numbers by using a hex examiner such as HxD. You can install HxD using chocolatey by running the following from a cmd prompt:
choco install -y hxd
Decrypting the WannaCrypted files
Just kidding. You can’t.
Actually, you can with two long-shots.
-
A decryption tool exists which can extract the prime numbers from memory which were used in the encryption. However, huge caveats: it relies on a Windows encryption implementation bug that only works for Windows OS versions less than 10, (e.g., XP through 7), and “it relies on current running memory so once you reboot it will be gone and if you’ve done too much on the system since infection, it’s possible the key won’t be found (because it’s been overwritten by data from other applications using the same memory space).”
-
Also, there’s a chance that if you pay the ransom, you will get a response… but, “Those who do shouldn’t expect a quick response – or any response at all. Even after payment, the ransomware doesn’t automatically release your computer and decrypt your files, according to security researchers. Instead, victims have to wait and hope WannaCry’s developers will remotely free the hostage computer over the internet. It’s a process that’s entirely manual and contains a serious flaw: The hackers have no way to prove who paid off the ransom.”
Indictment
In September 2018, the US Justice Department indicted a North Korean agent who participated in the WannaCry and Sony hacks.
References and Further Reading
- https://www.fireeye.com/blog/threat-research/2017/05/wannacry-malware-profile.html
- The Wannacry malware sample was originally obtained from https://www.malware-traffic-analysis.net/2017/05/18/index2.html – however, the original blog post has been archived. A wayback archive of the blog post can be found here (as of 2024-04-12).
- Read “Practical Malware Analysis – The Hands-On Guide to Dissecting Malicious Software” by Michael Sikorski and Andrew Honig. The book is accessible for beginners, and is also a handy reference for more advanced analysts.