Lab: Password Cracking
hydra, hashcat, rockyou, hashcat rules, cewl wordlists
- Kali
Part 1: Test Password Security
-
Visit the following URL:
https://lowe.github.io/tryzxcvbn/
This website estimates the strength of passwords you enter. Passwords never leave your browser – if you are so inclined, you can confirm as much by perusing the source code and/or by opening your browser developer tools and observing the (java)script that runs when you enter passwords.
-
Try out different passwords to see how strong they are.
Optional: If you want to learn more about password strength estimation, see this video and paper.
Part 2: Check an Account for a Prior Data Breach
-
Check to see if one of your online accounts has already been breached.
Visit: https://haveibeenpwned.com. Type in one of your email accounts or usernames to see if it has already been compromised in a data breach.
-
Next visit: https://haveibeenpwned.com/Passwords
Try out some passwords to see if they have already been compromised in a data breach.
-
Finally, visit: https://haveibeenpwned.com/NotifyMe
Sign up to be notified when one of your accounts is breached in the future.
Part 3. Sign-up for Two Factor Authentication
Visit https://2fa.directory/ and browse through the categories to find an online service that you regularly use (e.g., Gmail, Snapchat, Instagram, Facebook, online bank accounts, etc.). Sign up for 2FA for at least one account.
Also, visit dongleauth.info to find an online service that allows you to use WebAuthn or Universal Second Factor (U2F).
Part 4. Install and Set up a Password Manager
If you’re not already using one, set up a password manager. I recommend creating a free account with Bitwarden, or my favorite, 1Password (student discount link) with a small subscription fee. See here for a comparison of leading password managers.
Note: Read here for why I do not recommend using LastPass.
Next, install the browser extension for your password manager (see here for Bitwarden; see here for 1Password). With the browser extension installed, log into a website for which you have an account. Your password manager will ask to save the password after each login. Do this for three sites.
Deliverable:
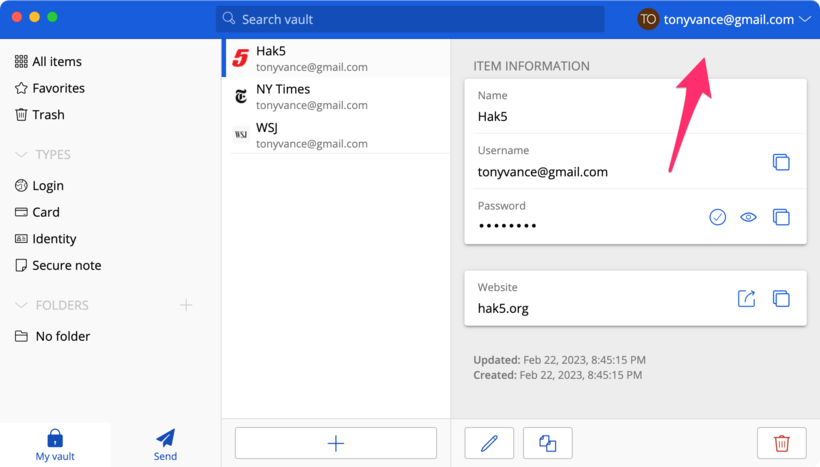
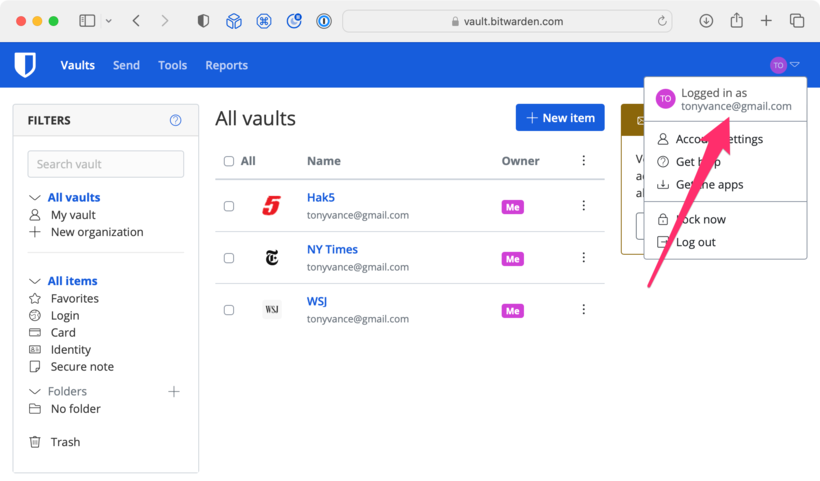
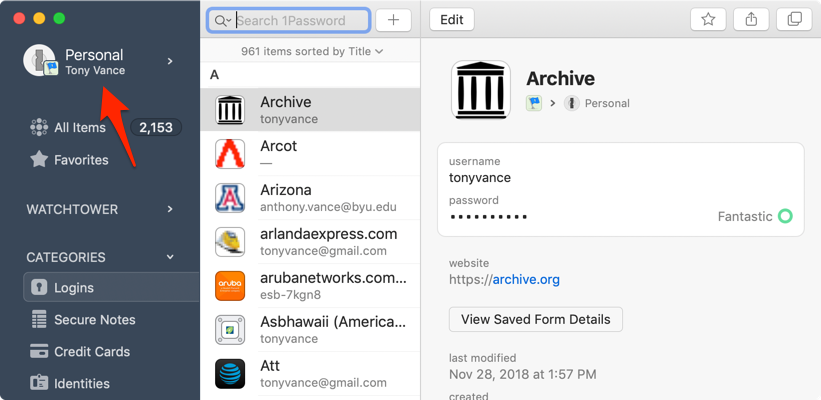
Take a screenshot of your password manager showing saved entries for at least three sites you visited. Also, make sure the screenshot shows your username in the top left- or right-hand corner. Submit your screenshot on Canvas.
Bitwarden app example screenshot:
Bitwarden.com example screenshot:
1Password app example screenshot:
1Password.com example screenshot:

Part 5: Online Password Attack
In this section, you will launch attacks over the network against login services, in an attempt to brute-force a username/password.
Note: This section uses the Kali VM.
This attack uses /usr/share/wordlists/rockyou.txt.gz, which comprises all unique passwords from the 32 million RockYou password breach.
-
Open a terminal and elevate to a root shell (or, alternatively, run all commands below with
sudo):sudo -sAccess denied?GCP is supposed to set you up with the ability to run
sudowithout a password. If that's not working and you get prompted for a password (there isn't one for your google login), then instead, elevate to a root shell by logging in as root with passwordtoor(root backwards), as follows:su root -
First, if the file
/usr/share/wordlists/rockyou.txtis not present, unzip the password list.gunzip /usr/share/wordlists/rockyou.txt.gz -
We will use the ‘rockyou’ password list to launch an online password attack using
THC-Hydra. The attack will be launched against a website that you run on your local Kali instance.Run the following commands from any directory to clone a repository to your Kali and then to use Docker to launch a web server.
git clone https://github.com/security-assignments/httpd-hydra-practice.git cd httpd-hydra-practice docker compose upA web server should now be running on port
9876. Visit http://localhost:9876 to confirm this.Now, visit http://localhost:9876/auth/ in a browser, and note that it requires a login. Let’s say that you wanted to crack the password for this route. Imagine that you knew, or guessed, that one of the usernames was
security-student.Type the following, all on one line (remember that you can use tab-completion for the rockyou path). Run the command after you read the explanatory text below the command on this page.
hydra -V -l security-student -P /usr/share/wordlists/rockyou.txt http-get://localhost:9876/auth/Note: The trailing slash (
/) in the final argument is needed.Where:
hydrais the password cracking tool to execute.-Vmeans verbose, and will show you the username and password combination being attempted.-l security-studentsets “security-student” as the login name. Note: that’s a lowercase ‘L.’-P /usr/share/wordlists/rockyou.txtis the password dictionary file to use.- the password is case-sensitive!
https-getmeans a GET request over HTTPS. Note that Hydra supports many protocols (e.g., ftp, ssh).localhost:9876/auth/is the password-protected URL to be accessed.
Tip This is a good opportunity to look at a command's built-in help documentation. Runhydra -hand peruse the output to find each of the above arguments, and read what they do. What would a lowercase-phave signified, instead of the uppercase-Pused? What would an uppercase-Lhave signified? Argument casing matters for this program!Note: you can also use THC-Hydra with web forms: http://insidetrust.blogspot.com/2011/08/using-hydra-to-dictionary-attack-web.html
In Greek and Roman mythology, Hydra is a mythical sea monster with many heads. When a head is cut off, it is replaced by another.
THC Hydra, the tool you are using, likewise launches multiple “heads” (tasks), each of which makes a battery of attacks (password guesses) before dying off and being replaced by another head (task). By default, Hydra runs with 16 concurrent heads.The Hydra output will tell you at what time it started, how many passwords it has tried so far, and at what time it stopped.
Question : Scan the results to find the line beginning with[9876][http-get]. What was the password?Question: Approximately how many passwords a second were you able to try? Hint: You may need to calculate this from the start and end time along with number of guesses made.
Question : For the lab submission, you will be asked to look at sample output from ahydrarun, and determine how many passwords were tried per second in the sample output.
Part 6: Offline Attack Using Hashcat
While in the previous section attacks were launched over the network, in this section, you will start with a password hash stored on your computer, and you will launch attacks against it locally. No authentication service such as a webserver sits in front of your attempts, potentially throttling the speed at which you can make guesses. Instead, you can make guesses as fast as your computer and the particular hash algorithm will allow.
If you're feeling adventurous, you can install Hashcat on your host computer, where you'll get massive speed improvements compared to running it in your Kali VM. Hashcast needs to be able to directly interface with the CPU/GPU in order to crack fast—it can't so as well in a virtualized environment.
For Windows or Linux, download Hashcat here. For Mac, I recommend that you first install Homebrew (follow instructions at https://brew.sh),
then run the command, brew install hashcat.
- On your Kali machine, open up a terminal and navigate to your home directory (
/root/). -
Hashcat uses a command-line interface. To see available options and syntax, type:
hashcat --help -
First, a dictionary attack will be performed against a password-protected Word document. The following command uses a Python script to obtain the hash of the Word document password called
hashcat.doc. This document has been prepared specifically for this lab. The word document has been password-protected. The hash of the password is stored within the metadata of the document file itself. You can use the Python script calledoffice2john.pyto extract the hash.johnin that script name refers to JtR, John the Ripper, and the Python script prints the hash in a format thatjohncan accept. We will edit the output to prepare for its use withhashcat.First, obtain the necessary files:
-
office2john.py can be obtained here. To obtain it in Kali, run:
wget https://raw.githubusercontent.com/magnumripper/JohnTheRipper/bleeding-jumbo/run/office2john.py -
hashcat.doc is available here. To obtain it, run:
wget https://raw.githubusercontent.com/deargle/security-assignments/master/labs/files/hashcat.doc
Then, run the following command from the directory to where you downloaded
office2john.pyandhashcat.doc:python office2john.py hashcat.doc -
-
In the output, you’ll see the name of the file, followed by the type. The type is shown with a
$at the beginning and end of it. You need to convert the output to a format thathashcatcan recognize. To do so, copy everything from the first$up to, but not including,:::.For example, if the script output was the following:
hashcat.doc:$oldoffice$1*04477077758555626246182730342136*b1b72ff351e41a7c68f6b45c4e938bd6*0d95331895e99f73ef8b6fbc4a78ac1a:::::hashcat.docYou would copy just the following to your clipboard:
$oldoffice$1*04477077758555626246182730342136*b1b72ff351e41a7c68f6b45c4e938bd6*0d95331895e99f73ef8b6fbc4a78ac1a -
While still in your home directory, run the following command (all on one line). Paste the hash string into the command, surrounded by single quotes (not double-quotes!).
hashcat --force -a 0 -m 9700 -o <your-output-filename> '<your-hash-string>' /usr/share/wordlists/rockyou.txtFor example, using the example hash from earlier, if I wanted my output to go to a file called
yay-output.txt:hashcat --force -a 0 -m 9700 -o yay-output.txt '$oldoffice$1*04477077758555626246182730342136*b1b72ff351e41a7c68f6b45c4e938bd6*0d95331895e99f73ef8b6fbc4a78ac1a' /usr/share/wordlists/rockyou.txtWhy not double-quotes? The hash includes$characters, which, inbash, when surrounded by double-quotes, are used to reference variables. This is unwanted here. Single-quotes prevents this.Once the password is cracked, read the contents of your output file to see the cracked password. It will be appended to the end of the hash following a colon (
:) symbol.Question : What is the password forhashcat.doc?
Peruse
man hashcatto get an idea of what the arguments do. In the above command, the switches correspond to the following:--forceThis is necessary to get hashcat to run in a VM environment (it doesn’t normally like to do so). -a 0Straight dictionary attack against the hash -m <Office_Flag>The corresponding flag for the version of Office in use (see table in hashcat --help)--statusProvides an update of the status of the process without giving a prompt -o <Output_File>The location where the cracked hashes will be saved.
The results will also be saved on the .pot file, unless otherwise specified. In our case, we disabled it.<Hash>The saved password hash. <Dictionary>The list of words that will be used to try and crack the password. -
Follow the same process as above, but this time for word doc file
john.doc(available here:wget https://raw.githubusercontent.com/deargle/security-assignments/master/labs/files/john.docQuestion : What is the password forjohn.doc? -
Examine the hashcat cracking benchmarks for a Sagitta Brutalis. The Brutalis has 8 graphics cards, each of which can simultaneously work on cracking hashes. The measured speed for each card is shown, along with a cumulative speed at the bottom (
Speed.Dev.#*). Use the cumulative speed for all Brutalis-related calculations in this lab.Cracking speeds are in the following format:
H/s Hashes per second KH/s Kilohashes per second (Thousands of hashes per second) MH/s Megahashes per second (Millions of hashes per second) GH/s Gigahashes per second (Billions of hashes per second) TH/s Terahashes per second (Trillions of hashes per second) PH/s Petahashes per second (Quadrillions of hashes per second)Hint: For the next two questions, use
ctrl+fin your browser on the benchmark report to find answers (e.g., search9600).Question : How many passwords per second can Hashcat running on a Brutalis try on a.docfile (i.e., hashtype “MS Office <= 2003 MD5 + RC4, oldoffice$0, oldoffice$1”)?Question : How much faster is Hashcat in cracking .doc MS Office documents (option 9700, “Hashtype: MS Office <= 2003 MD5 + RC4, oldoffice$0, oldoffice$1”) compared to Office 2013 documents (option 9600, “Hashtype: Office 2013”)?Question : How does an offline password attack compare with the online hydra attack you attempted earlier?Optional: Install
hashcaton your own machine (not the VM). See how your benchmarks compare against a Brutalis. Note that running benchmarks on the VM will break once it reachesscryptbefore complete results are reported.hashcat -b --force
Part 7. Cracking LinkedIn Hashes Using Hashcat
In this section, you’ll see how many hashes you can recover from the 2016 LinkedIn password breach. The LinkedIn hacker, a Russian, was sentenced in US court to seven years in jail on September 29, 2020. This breach of 177,500,189 unsalted SHA1 password hashes represents the data of all LinkedIn users as of 2012. Among these passwords, only 61,829,207 are unique.
However, in interest of your time, this section will require you to crack only 500,000 of these passwords. After you complete this lab, you’re welcome to crack all of the LinkedIn hashes. Ask me for a copy.
-
Download a copy of the file
LinkedIn_HalfMillionHashes.txtfrom here:wget https://raw.githubusercontent.com/deargle/security-assignments/master/labs/files/LinkedIn_HalfMillionHashes.txt -
To get your feet wet, perform a “straight” dictionary attack using the
rockyou.txtwordlist again. This attack will try each entry in the rockyou dataset with no permutations.Before you run the following command, read the
manpage to make sure you understand what each argument/switch does. Once you have done so, run the command.hashcat --force -m 100 --remove --outfile=LinkedIn_cracked.txt LinkedIn_HalfMillionHashes.txt /usr/share/wordlists/rockyou.txtNote: The above command may take 5–10 minutes to run. To see the status of a running job in Hashcat, press the
skey (it might take up to 15 seconds for Hashcat to report its status).hashcatwill report how many passwords it “recovered” when it finishes.These commands use the--removeflag. This will remove cracked hashes from the input file. So, if you run these commands more than once without changing anything, it won't crack anything after the first time.If you accidentally delete your cracked outfile, you will need to delete your hashcat "potfile" too before you try to recreate the outfile. You have to do this because otherwise, hashcat won't write any already-cracked hashes found in the potfile to the outfile. The
hashcat.potfileis stored in a hidden direction in the home directory of whomever you run the command as.To do this,
rm ~/.local/share/hashcat/hashcat.potfile.Don't forget to also start with a fresh 500k hashlist, because the
--removeflag would have removed rows from that file as the hashes were cracked and inserted into the potfile.To do this, first
rm LinkedIn_HalfMillionHashes.txt, and then rerun the earlierwgetcommand to fetch the hashlist again.You can always open another terminal session and count the number of lines in your outfile (
LinkedIn_cracked.txt) to see how many you’ve cracked so far, in total:wc -l LinkedIn_cracked.txtOr count the number of passwords left (it started with half a million):
wc -l LinkedIn_HalfMillionHashes.txtTo see hashes cracked in real time, in another terminal shell, type the command:
tail -f LinkedIn_cracked.txt. Typecontrol+cto exit thetailcommand.Question : How many passwords were you able to recover using the Hashcat command above? -
Run another attack that uses a rules-based method.
Rules apply common patterns to password dictionaries to crack even more hashes. You can read about rules in Hashcat here: https://hashcat.net/wiki/doku.php?id=rule_based_attack.
The “best64.rule” is one of the most effective sets of Hashcat rules. It is continually refined using input and testing from the password cracking community. You can view the contents of the best64.rule here, and an explanation of the rules here.
Run the following command once you understand what the
-rflag does.hashcat --force -m 100 --remove --outfile=LinkedIn_cracked.txt LinkedIn_HalfMillionHashes.txt -r /usr/share/hashcat/rules/best64.rule /usr/share/wordlists/rockyou.txtQuestion : How many total passwords were you able to recover after using this rules based attack in combination with the earlier straight attack? -
Run another attack that uses a hybrid method that uses a dictionary attack combined with a “mask,” which is a pattern that is appended to each password in the password dictionary:
hashcat --force -m 100 --remove --outfile=LinkedIn_cracked.txt LinkedIn_HalfMillionHashes.txt -i -a 6 /usr/share/wordlists/rockyou.txt ?d?dThe
?d?dat the end means to append two digits between 0–9 each at the end of each password in the rockyou.txt password dictionary.Question : How many total passwords were you able to recover after using this hybrid attack in combination with the earlier straight and rules-based attacks? -
If you would like to try using a different character set for your mask, you can use the following masks below. Note that each mask below is for one character. If you wanted to test four digits at the end of each password, the mask would be:
?d?d?d?d.?l = abcdefghijklmnopqrstuvwxyz ?u = ABCDEFGHIJKLMNOPQRSTUVWXYZ ?d = 0123456789 ?s = !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~ ?a = ?l?u?d?s ?b = 0x00 - 0xffOptional: Experiment with other rules found in
/usr/share/hashcast/rules.Optional: Another common password pattern is to prepend digits at the beginning of passwords. If you would like try this mask, run the following command:
hashcat --force -m 100 --remove --outfile=LinkedIn_cracked.txt LinkedIn_HalfMillionHashes.txt -i -a 7 ?d?d /usr/share/wordlists/rockyou.txt
Part 8. Secure Password Hashing
Refer again to the benchmark output for a Brutalis.
Hint: sites like WolframAlpha will do conversions for you. For example, see this example query for 70000 million / 150 thousand.
Read about the Bcrypt algorithm here, and also here
Part 9. Create a Targeted Wordlist Using CeWL
CeWL (Custom Word List Generator) is a command-line tool that creates custom wordlists from a target website. This can be useful for cracking a password of an organization or individual that also has a website or social media profile. Because people often use information about themselves or their organization when creating passwords, custom wordlists can be very effective.
Imagine that you exfiltrated the following MD5 hash from a database on
cf4aff530715824c055892438a1ab6b2
You want to create a custom dictionary using the words on neurosecurity.net to see if you can crack the hash.
-
Create a custom dictionary using CeWL for the website neurosecurity.byu.edu:
cewl -v -d 2 -m 5 -w custom_dict.txt https://neurosecurity.netWhere:
-vruns CeWL in verbose mode.-dis the depth to “spider” or crawl the website-mis the minimum word length-w custom_dict.txtis the name of your new custom wordlist or dictionary.
Give the command a minute or two to complete.
-
Check how many entries are in the
custom_dict.txtfile:wc -l custom_dict.txt -
Look at the words in
custom_dict.txt:less custom_dict.txt -
Permute the words in the
custom_dict.txtwordlist using the “best64” rule, and append the output tocustom_dict.txt(all one line):hashcat custom_dict.txt -r /usr/share/hashcat/rules/best64.rule --stdout >> custom_dict.txt -
Check how many entries are in the custom_dict.txt file now:
wc -l custom_dict.txt -
Run Hashcat using custom_dict against the MD5 hash (all one line):
hashcat --force -a 0 -m 0 cf4aff530715824c055892438a1ab6b2 custom_dict.txtWhere
-m 0signifiesmd5mode, and-aspecifies “straight attack mode” (do not permutate the wordlist, because we already did)The password will be reported towards the top of the output in the format:
hash:password. If you miss the output, you can view it in your potfile once you have cracked it by runninghashcat --show cf4aff530715824c055892438a1ab6b2 -
Confirm that you found the correct password:
echo -n "<the plaintext password>" | md5sumWe include the
-nflag because otherwise, theechocommand will append a newline character, which will throw off the hash.
Learn more:
- Podcast: Story behind the game-changing RockYou password breach: https://darknetdiaries.com/episode/33/
- “Hash Crack: Password Cracking Manual (v3)” by @Netmux, one of the foremost password crackers.
- https://arstechnica.com/security/2013/03/how-i-became-a-password-cracker/
- Official Hashcat documentation: https://hashcat.net/wiki/