Introduction to Networking
Attribution: This page is based on an activity developed by Jennifer Urban and Chris Hoofnagle at UC Berkley.
Do the following activities to help you learn about networking.
Traceroute
The Traceroute command shows the network route or path between your computer and another device on the internet or network.
-
From your computer or Kali Linux VM, open a terminal.
On a Mac, you can do this by clicking command & the space bar and typing
terminal. In Linux and Mac, the command istraceroute.On Windows, search for
cmdand press enter. A terminal window should open. On Windows, the command istracert. -
Type:
traceroute yahoo.comLook at all the “hops” of your request to “trace the route,” or in other words, follow the path of your request between your computer and one of Yahoo’s servers.
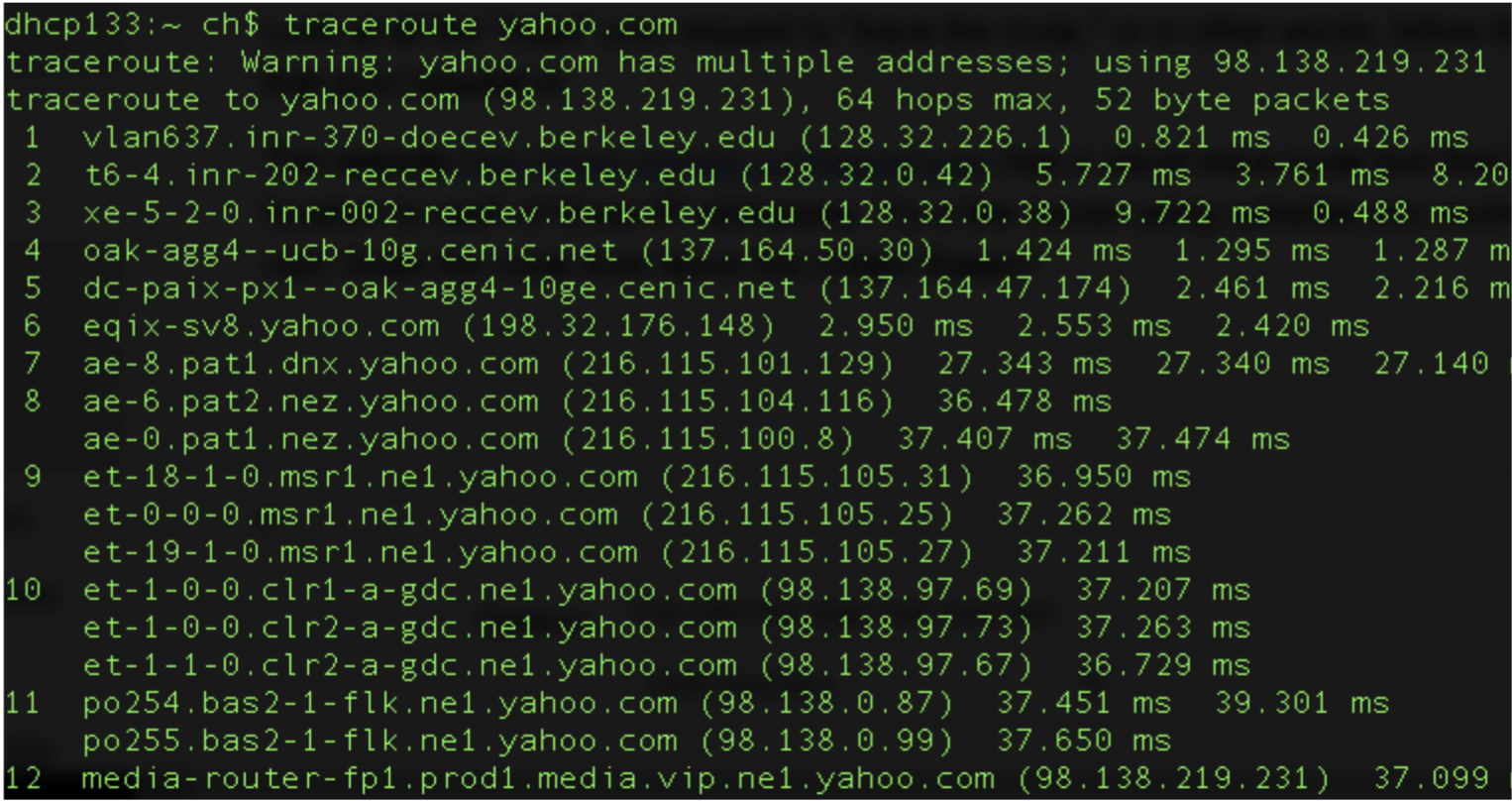
Questions:
What does all this hopping mean for cybersecurity?
What does it mean that Yahoo has “multiple addresses?”
Can you ascertain anything about the location of each of the “hops” mapped on your traceroute? Look, for example, for airport codes or other geographic identifiers (e.g., “oak” in the above example, or “lhr” for London Heathrow, “jfk” for John F. Kennedy airport in New York, “iad” for Dulles airport in DC, etc).
You can also use tools to help decipher this. The website traceroute-online.com has visual trace route tools that links location to each of those IP addresses. Try a few traces using websites you routinely visit. Do the hops on the route ever leave the United States?
Email Headers
Another way of illustrating the “hops” that data make online is to look at email headers. You can do this in Gmail by clicking on the little menu in a message and selecting Show Original.
Focus on the “Received: from” lines. Your email makes hops on the internet, probably in plain text format.
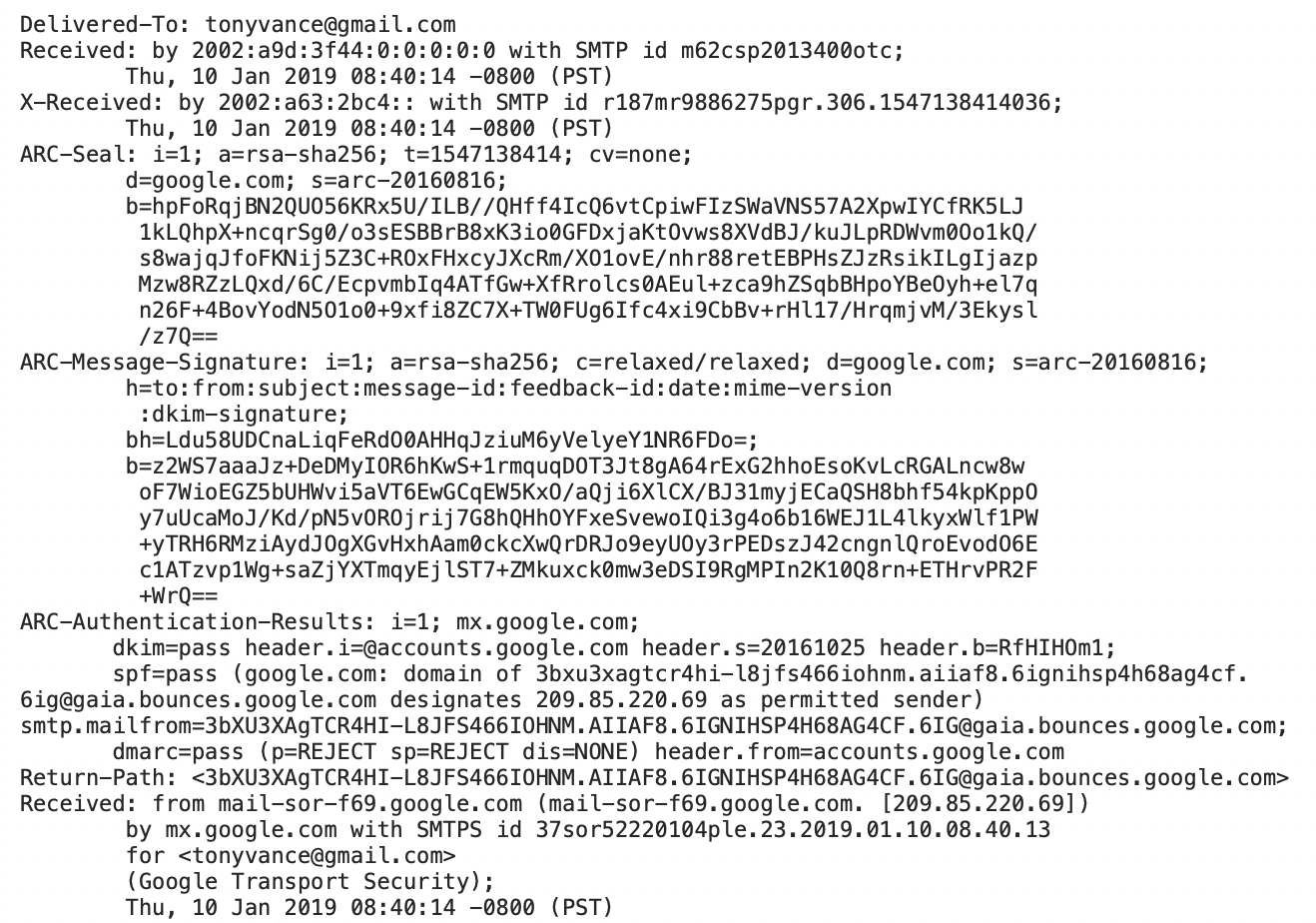
Compare several different messages. Are there more or less “Received” lines on your email sent by other people who use Gmail than competing services? What does it mean for cybersecurity that most email now goes from one Google user to another Google user?
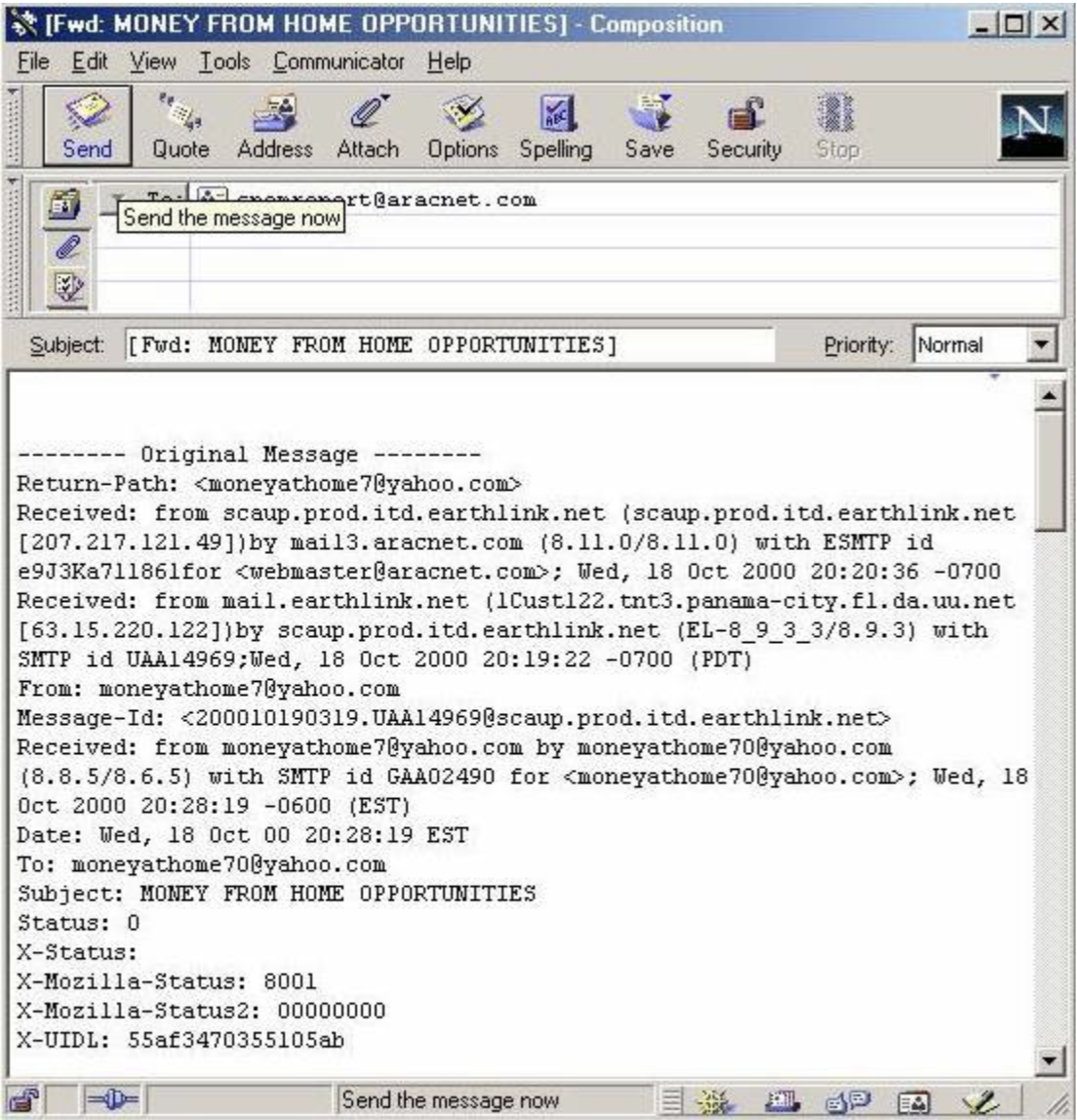
As a comparison, here are two old email headers. Notice how more servers are listed in the “Received from” lines? This means that more parties unrelated to the communication had the opportunity to “read” or otherwise infer knowledge from the email.
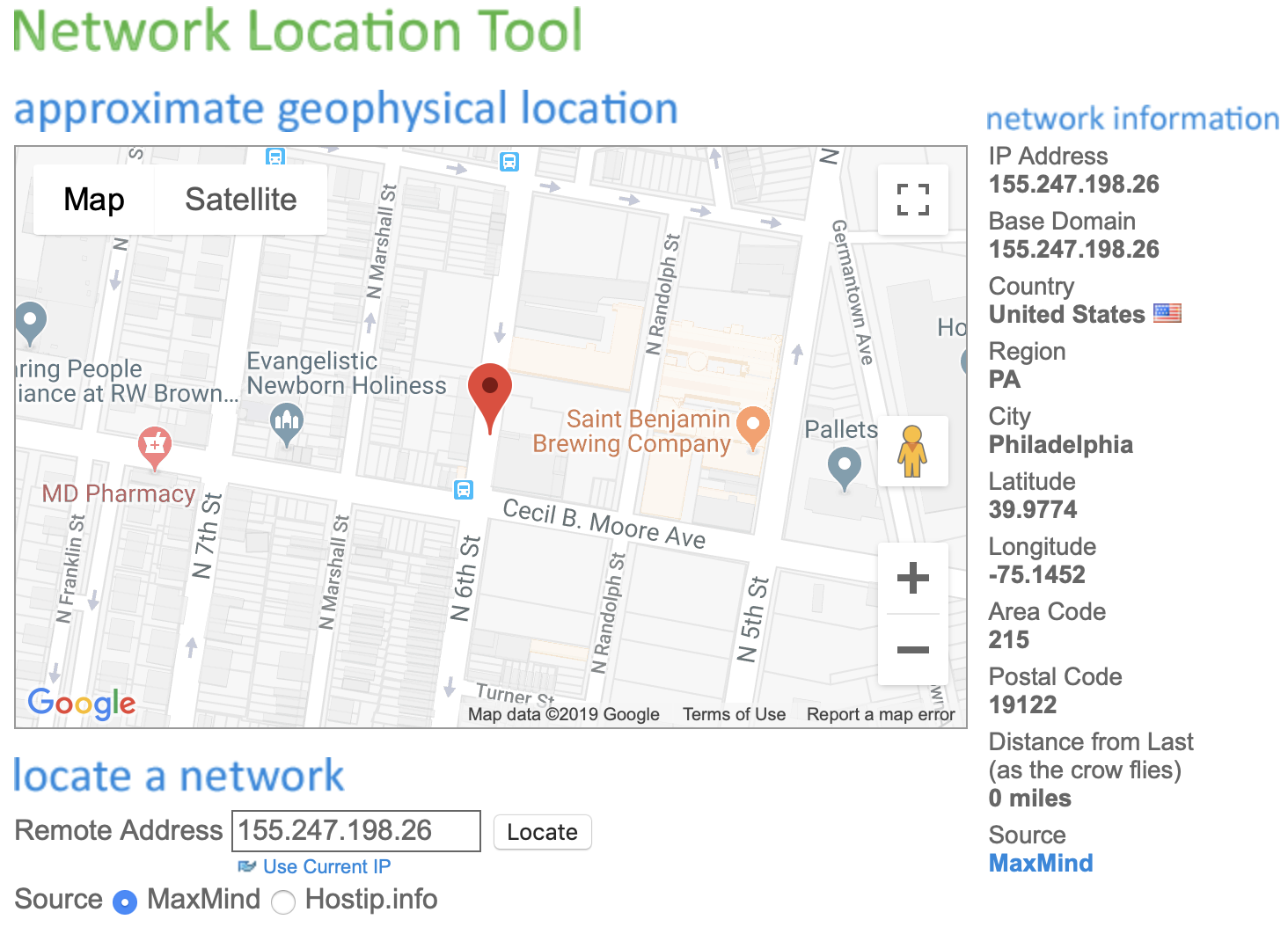
Physical location on the internet
Try this exercise at school and at home. Visit https://www.yougetsignal.com/tools/network-location/. The “Remote Address” field is your public, the IP address that servers on the internet can see. Click the Locate button.
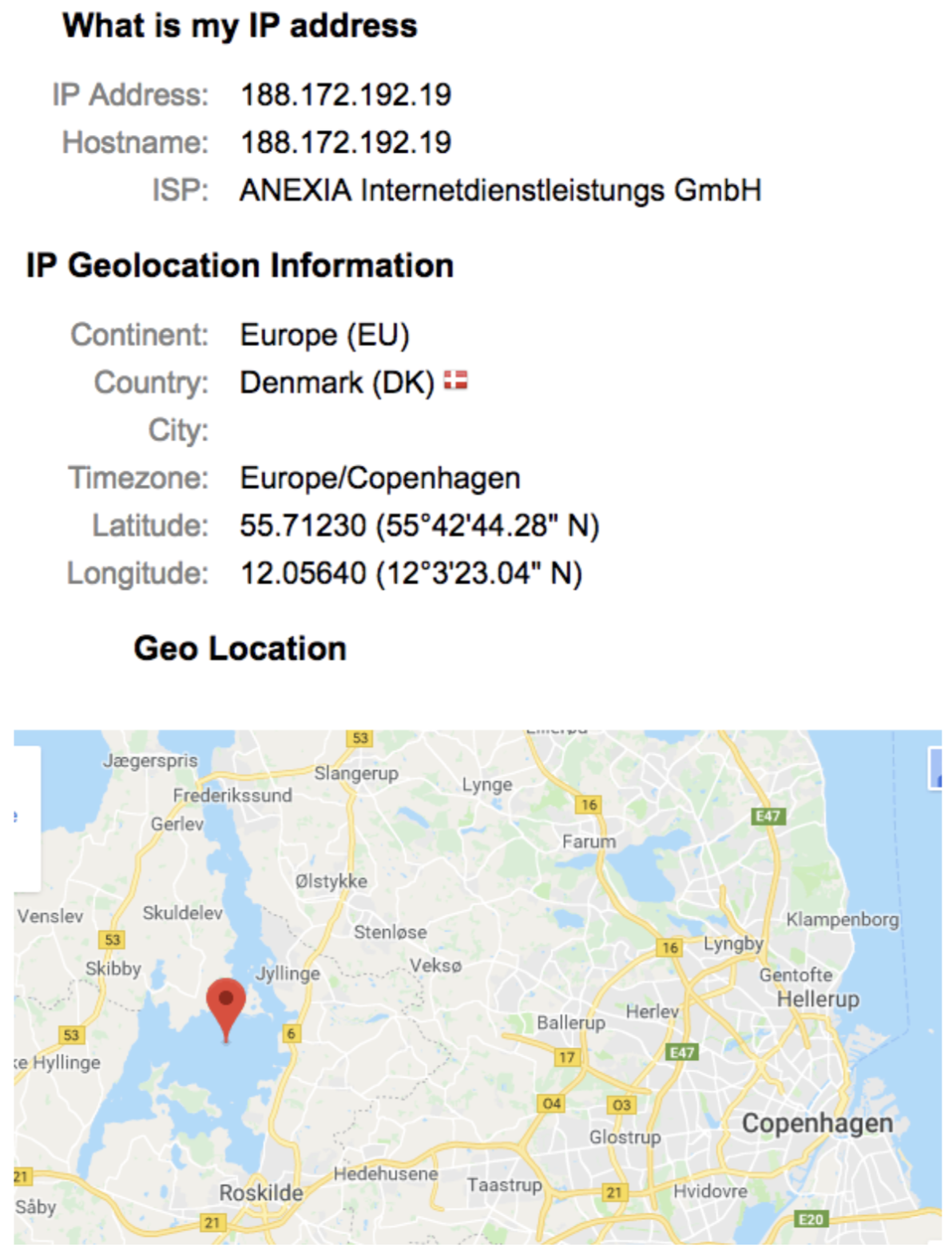
And if one uses a Virtual Private Network (VPN), one can encrypt their internet traffic and cause it to “tunnel” to another place in the world. Application-layer services then interpret this traffic to come from another country entirely.
Now, consider what it means that one could use multiple VPNs, or a browsing system that automatically routes service traffic in circuitous ways, such as Tor (this site may not be accessible from certain networks).
More about IP addresses
Open a Microsoft Word document and record your answers to the following questions. You can also take screen shots and paste it into your document to explain your answers.
- What is the public IP address for Temple.edu?
- What class of IP address is the IP address for Temple.edu?
- What is the IP address for your Metaploitable2 VM?
- What is the IP address for your Windows VM?
- Is the IP address for your Windows and Metasploitable 2 VMs public or private?
- How would you test communication between two devices?
- What protocol is commonly used on the internet?
- Use the following tools–
netstat,dig,nslookup, andping–to examine the IP address for Temple.edu and explain how these tools can be beneficial to a security professional. Take screenshots to show you have answered the above questions and add them to document you will submit.
Shodan
As we connect more and more devices to the Internet, we create an “Internet of Things” (IoT). These things include webcams, doorbells, thermostats, and anything else that can connect over IP.
The economics of IoT run against secure practices. Security adds cost, slows development, and degrades critical functions such as energy preservation. Thus, many IoT devices are woefully insecure and remotely exploitable.
To get an idea of the scope of the problem, we have a simple exercise for you—explore the website Shodan.
Shodan is a service that scans the open Web, looking for services. It provides a search engine for finding services, including insecure ones. For instance, this search reveals all IP-connected devices/services that signal the presence of a default password.
From an attacker’s perspective, one could use Shodan to locate vulnerable devices and exploit them. For instance, one could search for common vulnerabilities, on sites such as MITRE’s, and then look for susceptible devices on Shodan.
You can also do a simple check of your home’s internet security. Start by determing your IP address. You can do this now with a simple Google search: What is my IP address? (it should be something like 68.86.10.67–if it looks very different, such as “2600:1600:be50:a530:11ab:5224:c0ff:e33c”, you have an IPv6 address). You can also find your IPv4 address at services such as https://whatismyipaddress.com/.
Paste your IPv4 address into Shodan. Are any services showing up as available?