Lab: Web Privacy and Anonymity
Overview of trackers, third party cookies, and Tor
This lab will help you learn more about how to protect your privacy on the Web. Perform the steps below on your personal computer, not your Kali VM on Google Cloud.
Part 1: Check Out Your Data
Several major companies allow you to check out and examine the data they have on file for you. This can be very revealing.
Use this link to learn how to download your data from one or more of the following services:
- Facebook (highly recommended)
- Google (If you use Gmail or Google Drive, note that downloads can be large)
Alternatively, see the links below to download your data from these companies:
If you aren’t a customer for any of the above companies, try to check out your data for another company you use.
Part 2: Blocking Web Trackers
Although ad trackers are seemingly everywhere on the Web, the good news is that the newest versions of several major web browsers–such as Firefox, Brave, and Safari for Apple devices–have built-in privacy protections.
Setup Firefox
For this section of the lab, you’ll configure Firefox on your laptop to block and examine web trackers of various kinds.
- Watch this one-minute video about the privacy protections in Firefox.
- Make sure you have at least Firefox 70
- If you don’t already have Firefox, download the latest version of Firefox.
-
If you already have Firefox installed on your laptop, check to see that you have Firefox 70 or later installed.
To do this, visit the “About” page. Visiting this page downloads any available updates.
- On a Mac, go to the Firefox menu and select “About Firefox.”
- On Windows, go to the “Help” menu and select “About Firefox.”
If an update was downloaded, after it finishes, click the “Restart to update Firefox” button.
- Turn on fingerprint blocking.
- Open Firefox preferences by clicking the icon with three horizontal lines (the so-called “hamburger” icon) in the top-right-hand corner of Firefox.
- Select “Privacy & Security”
- Under “Enhanced Tracking Protection,” select “Custom,” and make sure that all four boxes are checked (“cookies,” “Tracking content,” “Cryptominers,” and “Fingerprinters”.
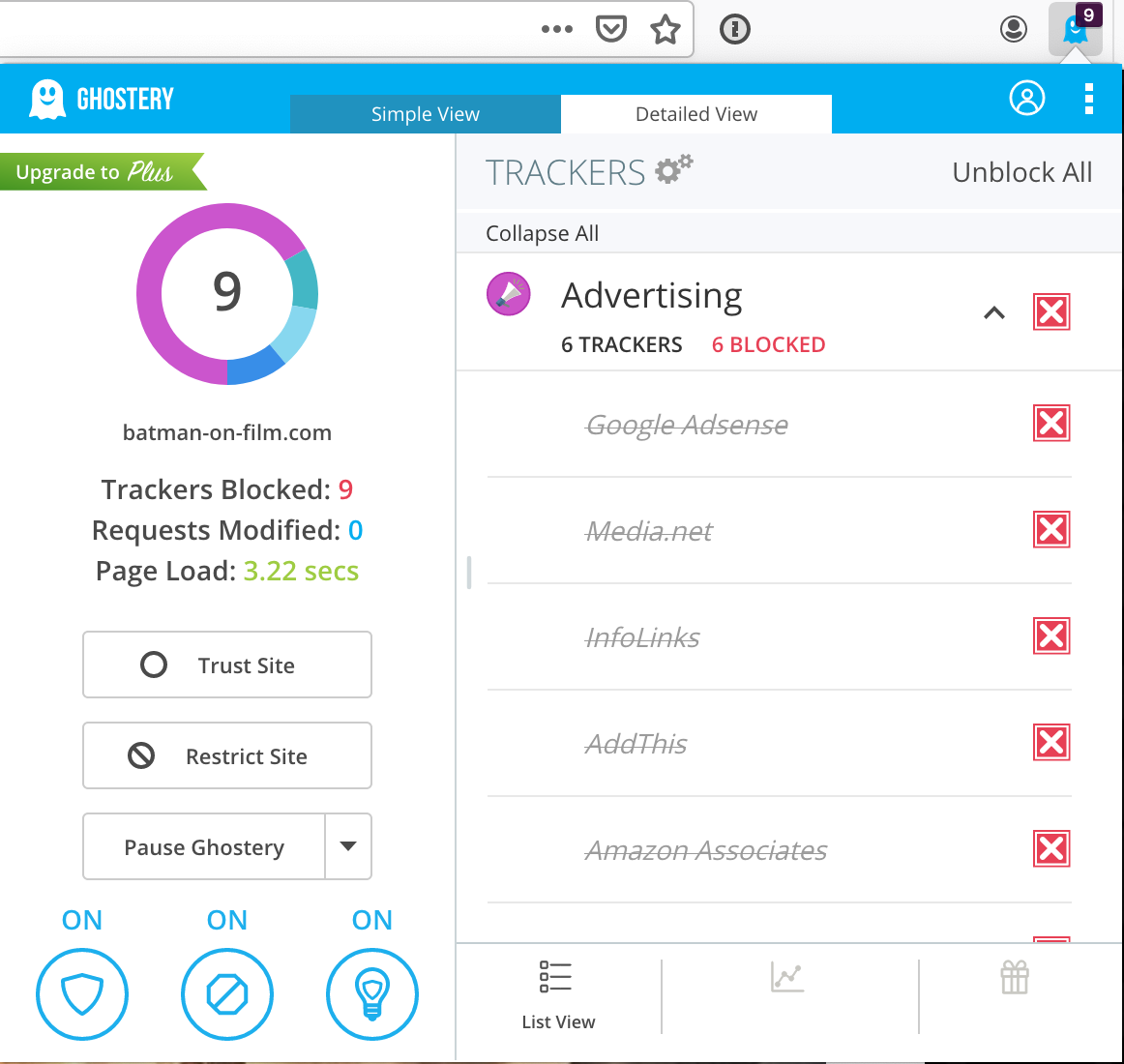
Use Ghostery to Learn about Web Trackers
Firefox now blocks third-party cookies and fingerprinting techniques. However, to get more information about web trackers, you’ll next install Ghostery, a browser extension that blocks ads and trackers.
- Visit https://www.ghostery.com/ghostery-ad-blocker and install the Ghostery extension in Firefox.
- In “Customize Setup,” select “Block Everything” and click the “Next” button. Uncheck the box for sending anonymous analytics to Ghostery.
- Browse to your favorite sites and click the Ghostery icon after each page load. Which of your favorite sites uses the most web trackers?
-
Click on the Ghostery icon and select the “Detailed View” tab. Click on the struck-through name of an add tracker and, if available, click the “Continue to full tracker profile” to learn more about the ad tracker (see figure below).
-
Google “privacy policy” and the name of one of the trackers you identified to read about that tracker’s privacy policy.
Question : What is the name of the third-party tracker you read about, and what kinds of information is its company collecting about you?
Part 3: Browser Fingerprinting
-
Visit Coveryourtracks.eff.org and click the “Test your browser” button. Leave the “Test with a real tracking company” option checked.
Question : Is your browser blocking tracking ads?Question : Is your browser blocking invisible trackers?Question : Does your browser protect against fingerprinting? -
In the
Detailed Resultssection of the report, look at the different kinds of metrics to see how many bits of identifying information each one provides.Note: The bits of identifying information means that your browser can be uniquely identified out of a set of 2^bits of identifying information. A lower score is better, because it means that you can be less precisely identified. For example:
“We observe that the distribution of our finger- print contains at least 18.1 bits of entropy, meaning that if we pick a browser at random, at best we expect that only one in 286,777 other browsers will share its fingerprint. Among browsers that support Flash or Java, the situation is worse, with the average browser carrying at least 18.8 bits of identifying information. 94.2% of browsers with Flash or Java were unique in our sample.”
https://coveryourtracks.eff.org/static/browser-uniqueness.pdf
Question : How many bits of identifying information does Coveryourtracks.org report for your browser?
Part 4: Anonymous Web Browsing
There are occasionally times when anonymity on the internet is desirable. This is different from confidentiality on the internet. With confidentiality, it is not possible for eavesdroppers to read the web traffic. With anonymity, web traffic cannot be linked back to its origin.
HTTPS provides web traffic confidentiality – but only of the request
content. Web traffic elements such as the source and destination IP, and DNS
requests, are public. This means that if a political activist uses a computer
with IP address 192.0.2.1 and logs in to
https://securedrop-for-journalists.example.com/submit/something/condemning and
submits leaked documents, the following information should be encrypted
(confidential):
- The login information
- The submitted documents
- That the requested path was
/submit/something/condemning
However, https cannot protect the following information:
- The source IP address of
192.0.2.1 - The request to
securedrop-for-journalists.example.com
The latter is considered “metadata,” and it must be readable for the internet to work. However, it alone may be enough to identify and implicate the activist. Internet service provider records can associate an IP address with a specific street address, which can be used to point to a human.
But if the source IP address could be obfuscated, then while an eavesdropper
would still see a connection to securedrop-for-journalist.example.com, the
activist would remain anonymous.
Some might use VPNs to try to anonymize their IP addresses. While this hides web requests from immediate surveillance at the request origin network level (e.g., hides the traffic from an ISP), it is still possible to get the true source IP via VPN server logs. One might attempt to mitigate this attack by using several VPN servers in a chain, but the attack still exists.
Testing whether private browsing anonymizes source IPs
- Go to https://whatismyip.com/ and note your IP address.
- Turn on your browser’s privacy mode (e.g., “Incognito Mode” in Chrome, “Private Browsing” in Firefox and Safari).
- Go to https://whatismyip.com/ again and note your IP address.
Note that your IP address didn’t change. Why not?
What is Tor?
One of the main goals of Tor is to anonymize source IP addresses.
The Tor browser uses encryption techniques to tunnel your traffic through
several Tor “nodes” (usually 3). Each node only knows the one that comes before
it and after it in the chain. Traffic originating from a Tor client connecting
to securedrop-for-journalist.example.com would do something like the
following:
- The client chooses its Tor node chain.
- The client wraps its web request, including the chain information, in a series of “onion” layers of encryption.
- The client passes its request to the first node in the chain, termed the entry node. The entry node removes the first layer of encryption, and passes the encrypted traffic on to the next Tor node.
- The nodes repeats the steps of removing an encryption layer and pass-along, until ultimately the traffic leaves the Tor network via the last node in the chain, termed the exit node.
- The exit node makes the direct web request to the
securedrop-for-journalist.example.comserver, on behalf of the originating Tor client. Any response fromsecuredrop-for-journalist.example.comwould pass in reverse through the Tor network, back to the Tor client via the entry node.
Optionally, if the request is to a special .onion domain, the traffic is
actually intended for a server within the Tor network, which is only
accessible via the Tor network. In this case, the traffic never exits, and
therefore never travels over public internet protected potentially only by HTTPS
encryption. When the traffic stays in the Tor network, the final step is still
wrapped in an “onion” layer of encryption.
Testing whether Tor anonymizes the source IPs
In this section, you will use the Tor Browser.
The Tor Browser can be used from your own computer, or it can be used from the Kali-on-GCP instance.
-
Install Tor if necessary: available for Linux, Mac, and Windows here.
To install Tor on Kali, read this guide.
Note: You might not be able to download or use Tor Browser on your university's campus network unless you use a VPN service. If this is your case, then you can use the Tor browser from an off-campus network.Note: If you’re using a Mac and MacOS refuses to open the Tor Browser app because it is from an unknown developer, hold the control key and right-click the Tor Browser app and then select “open.” This will create an exception for the Tor Browser app and open it. - Run the Tor Browser.
- Visit https://whatismyip.com/ inside of the Tor Browser and verify that your IP address has changed.
- Determine your IP address using three different websites (e.g., https://www.whatismyip.com/, https://www.whatsmyip.org, and https://whatismyipaddress.com/). Note what IP addresses each site reports for your browser.
-
Look up the location of each IP address you noted in step 6 using a service like https://www.wolframalpha.com/.
Question : To which parts of the world do the IPs you noted in step 5 belong? - Read this page about what Tor can and can’t do to protect your anonymity: https://support.torproject.org/faq/staying-anonymous/
Visit an .onion server
As noted earlier, Tor also provides the ability to access servers that are only accessible via the Tor network. This is what is known colloquially as “the dark web.” While it’s true that there are many sites providing illegal services on the dark web, there are also legitimate uses for the dark web as well.
Read this short article about the dark web: https://www.wired.co.uk/article/what-is-the-dark-web-how-to-access/
Access legitimate Tor services
Access some legitimate Tor services using the Tor browser:
SecureDrop
Many news organizations use SecureDrop to “securely accept documents from anonymous sources,” such as from whistleblowers.
Visit the SecureDrop FAQ to read about how SecureDrop works.
Then, use the SecureDrop directory to find and visit the drop sites for each of the following news organizations:
- The New York Times
- The Washington Post
- ProPublica
If you have a Facebook account, you can access Facebook using their TOR service:
https://www.facebookwkhpilnemxj7asaniu7vnjjbiltxjqhye3mhbshg7kx5tfyd.onion/
Facebook says the following about why it provides an onion address:
Consider Tor: Tor challenges some assumptions of Facebook’s security mechanisms - for example its design means that from the perspective of our systems a person who appears to be connecting from Australia at one moment may the next appear to be in Sweden or Canada. In other contexts such behaviour might suggest that a hacked account is being accessed through a “botnet”, but for Tor this is normal.
Note: Facebook says that as of April 2016, more than 1 million people access Facebook via Tor
The Federalist Papers
Originally published pseudonymously in 1787–1788:
http://kx5thpx2olielkihfyo4jgjqfb7zx7wxr3sd4xzt26ochei4m6f7tayd.onion/book/9K0biYYOZKvPBokZ
The New York Times
https://www.nytimesn7cgmftshazwhfgzm37qxb44r64ytbb2dj3x62d2lljsciiyd.onion
ProPublica (non-profit news site)
http://p53lf57qovyuvwsc6xnrppyply3vtqm7l6pcobkmyqsiofyeznfu5uqd.onion
DuckDuckGo search engine
https://duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion
The CIA’s official Tor service
http://ciadotgov4sjwlzihbbgxnqg3xiyrg7so2r2o3lt5wz5ypk4sxyjstad.onion
OnionShare
Anonymously send and receive files, chat, and host websites via the Tor network using OnionShare:
http://lldan5gahapx5k7iafb3s4ikijc4ni7gx5iywdflkba5y2ezyg6sjgyd.onion/
.onion without a Tor client
Try to load a .onion URL in a browser other than the Tor Browser.
Overall
We will never be able to de-anonymize all Tor users all the time... [but] with manual analysis we can de-anonymize a very small fraction of Tor users, however, [never in response to a post-hoc request].