Virtual Machines for the Security Labs
This page documents virtual machines that I have prepared for students in my class to use to complete the labs.
Setting up your virtual lab
I have created a Kali virtual machine image on Google Cloud Platform which is using nested virtualization to host within it several virtual machines:
a Windows instance, a Metasploitable2 instance, and a security onion instance. They are hosted using kvm and libvirt and accessed using virt-manager.
Read these instructions to get oriented to and set up on Google Cloud Platform, and to get access to the Kali virtual machine. Anyone should be able to see and use the custom class kali image if they join this Google Group (public access):
infosec-net Network Map
The network map is as follows:
| IP Address | Machine | Login | Password | Notes |
|---|---|---|---|---|
| 192.168.56.101 | Kali (the host) | root |
toor |
|
| 192.168.56.100 | Windows VM | Labuser |
Passw0rd! |
This VM is memory-intensive! Will probably freeze and not launch if your GCP instance doesn't have at least 8 GB memory. |
| 192.168.56.102 | Metasploitable2 VM | msfadmin |
msfadmin |
|
| 192.168.56.103 | Security Onion VM | securityonion |
Password1 |
This VM is memory-intensive! |
IPv4 network block in CIDR block notation: 192.168.56.0/24
Using the virtual machines within Kali
-
The virtual machines are accessed using
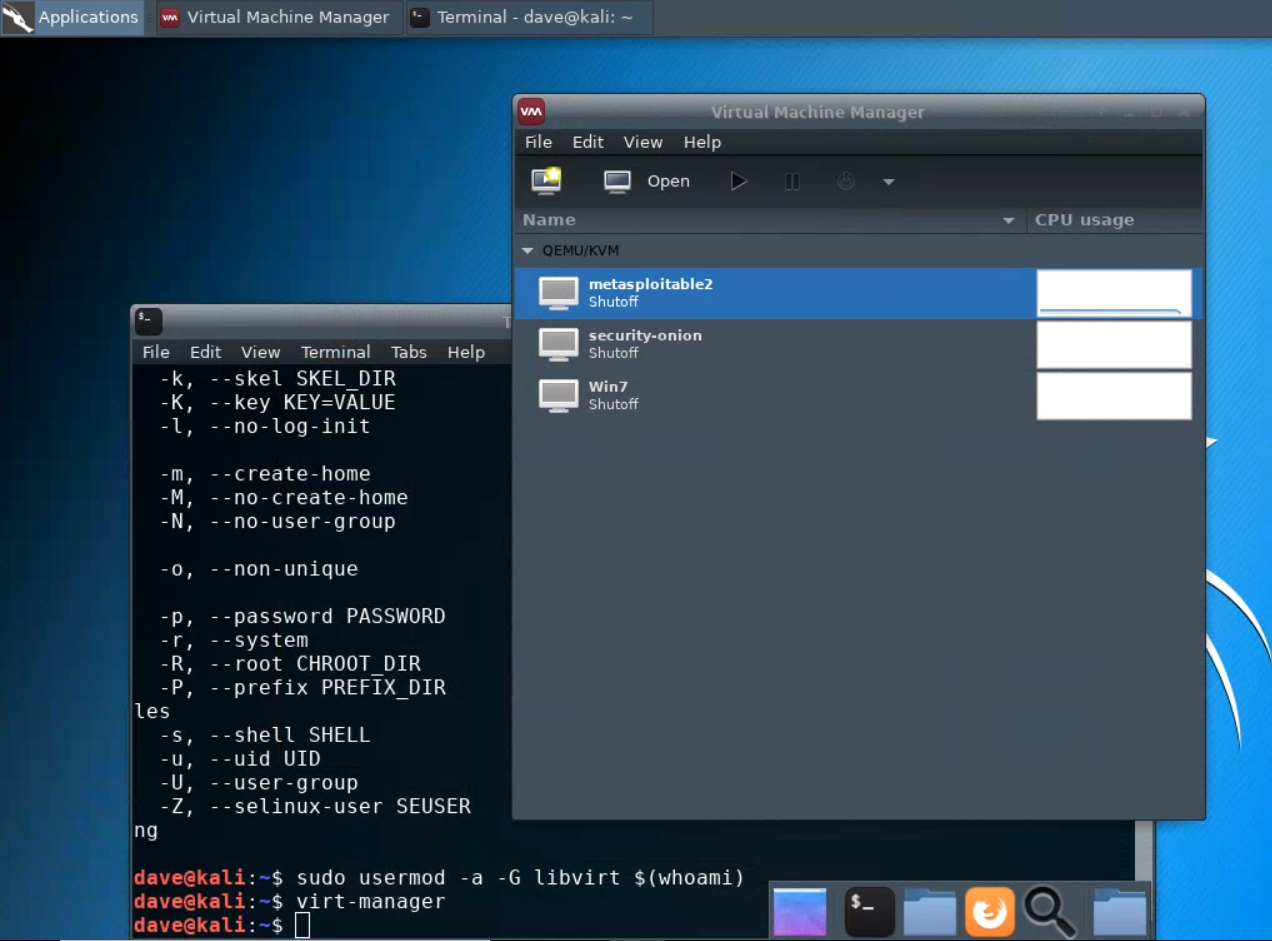
virt-manager. First, you should make sure that your user account is a member of thelibvirtgroup.sudo usermod -a -G libvirt $(whoami)Heads up! This will need to be run each time you create a new Kali instance.Alternatively, log in as root (password
toor):su root -
Then, from a terminal, run
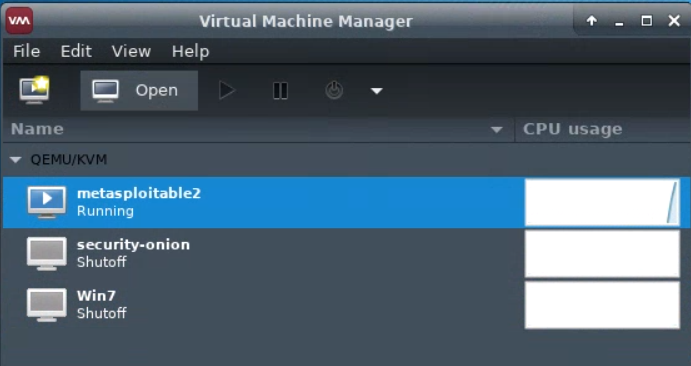
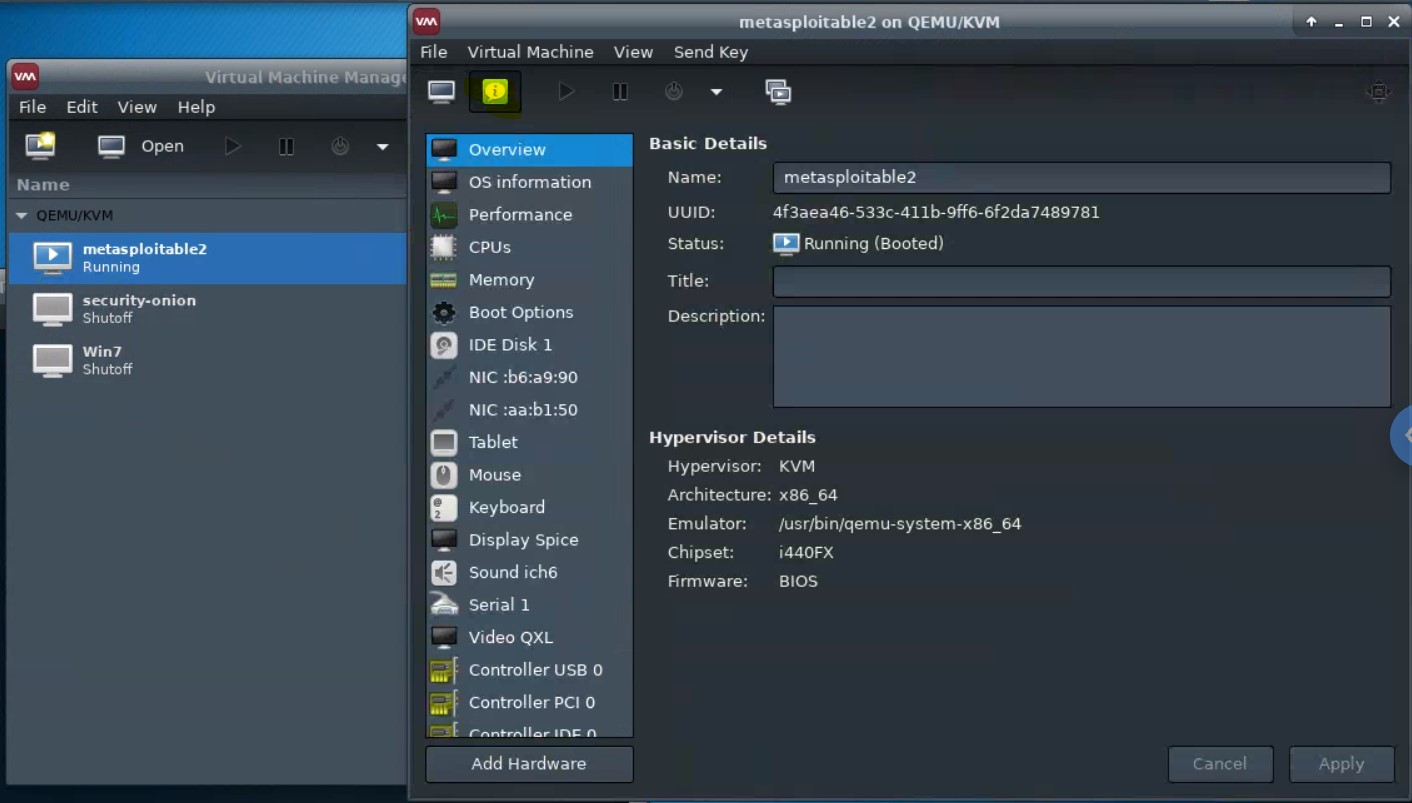
virt-managerto get an interface such as the following:This shows that three virtual machines are available, but that none are running.
Virt Manager interface shows no vms?In the
virt-managerinterface, try running:FileAdd Connection...Connect (accept defaults)
Starting and accessing virtual machines
-
Start a virtual machine by selecting it, and pressing the “play” icon. The virtual machine should then update to show that it is running.
-
To view the running virtual machine, highlight it and click “Open”. A new window will appear.
You can click into this window and interact with it via keyboard, and mouse if it has a GUI.
-
Details of a virtual machine can be viewed and edited from the “details” pane.
-
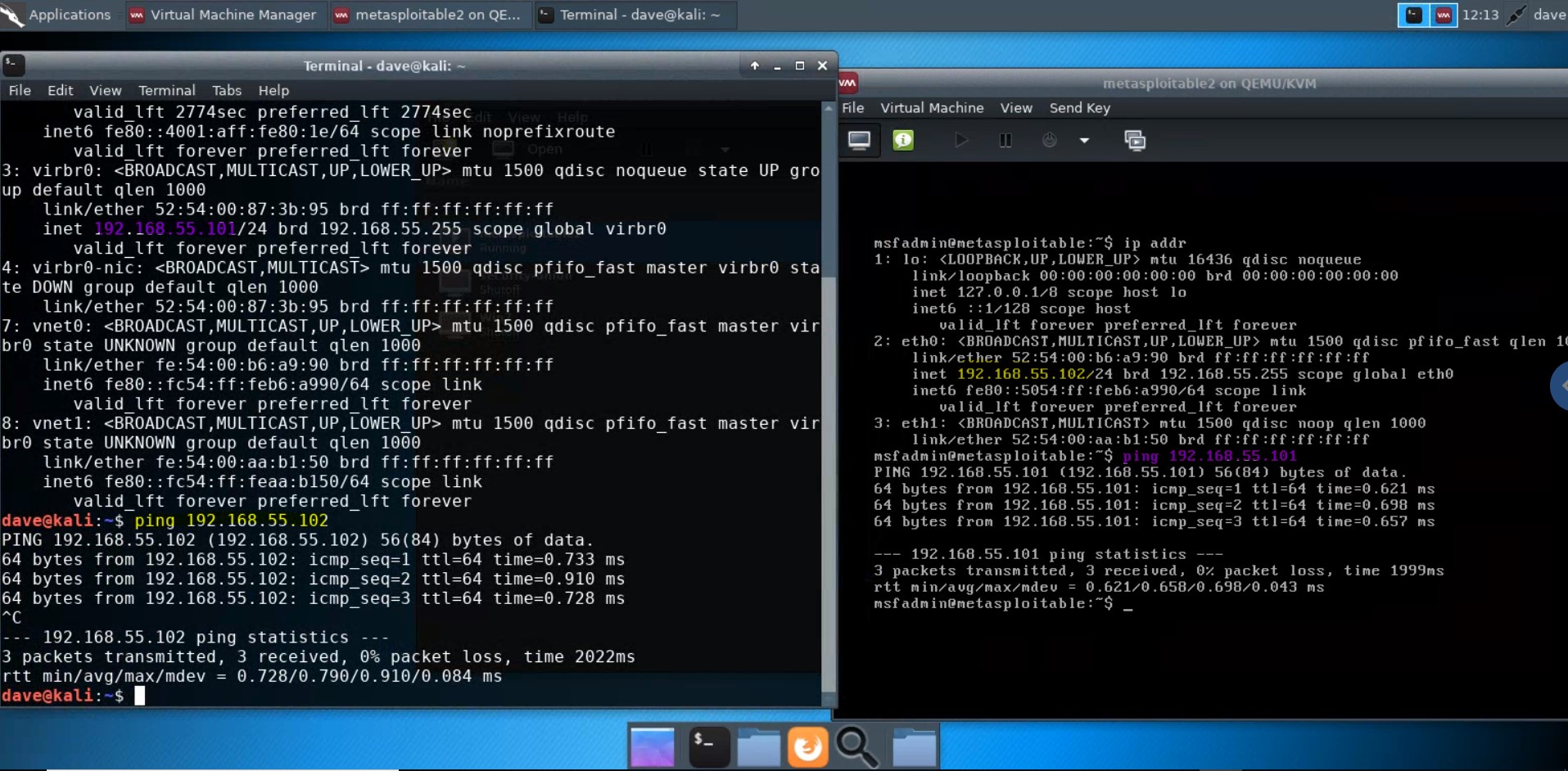
A network is set up to enable the host (Kali) and the guests (e.g., Metasploitable2, Windows 7) to network with one another. Try
pinging metasploitable2 from Kali, and Kali from metasploitable2, using the network map ip addresses above.
Updating the virtual machines
The following scripts will update the respective lab virtual machines installed on the kali pentest lab image.
Update SecurityOnion
To update Security Onion, run the following:
wget -O - https://raw.githubusercontent.com/deargle/kali-xfce-gcp-qemu-packer/master/kali-pentest-lab/update-securityonion.sh | sudo bash
Update Windows Server 2019
To update Windows Server 2019, run the following:
wget -O - https://raw.githubusercontent.com/deargle/kali-xfce-gcp-qemu-packer/master/kali-pentest-lab/update-server2019.sh | sudo bash
Update Metasploitable2
To update Metasploitable2, run the following:
wget -O - https://raw.githubusercontent.com/deargle/kali-xfce-gcp-qemu-packer/master/kali-pentest-lab/update-metasploitable2.sh | sudo bash
Using snapshots
Virtual machines in virt-manager can be “snapshotted”, which lets you restore the virtual machine to a previous state if you mess it up by doing something such as deploying malware to it.
Creating a snapshot
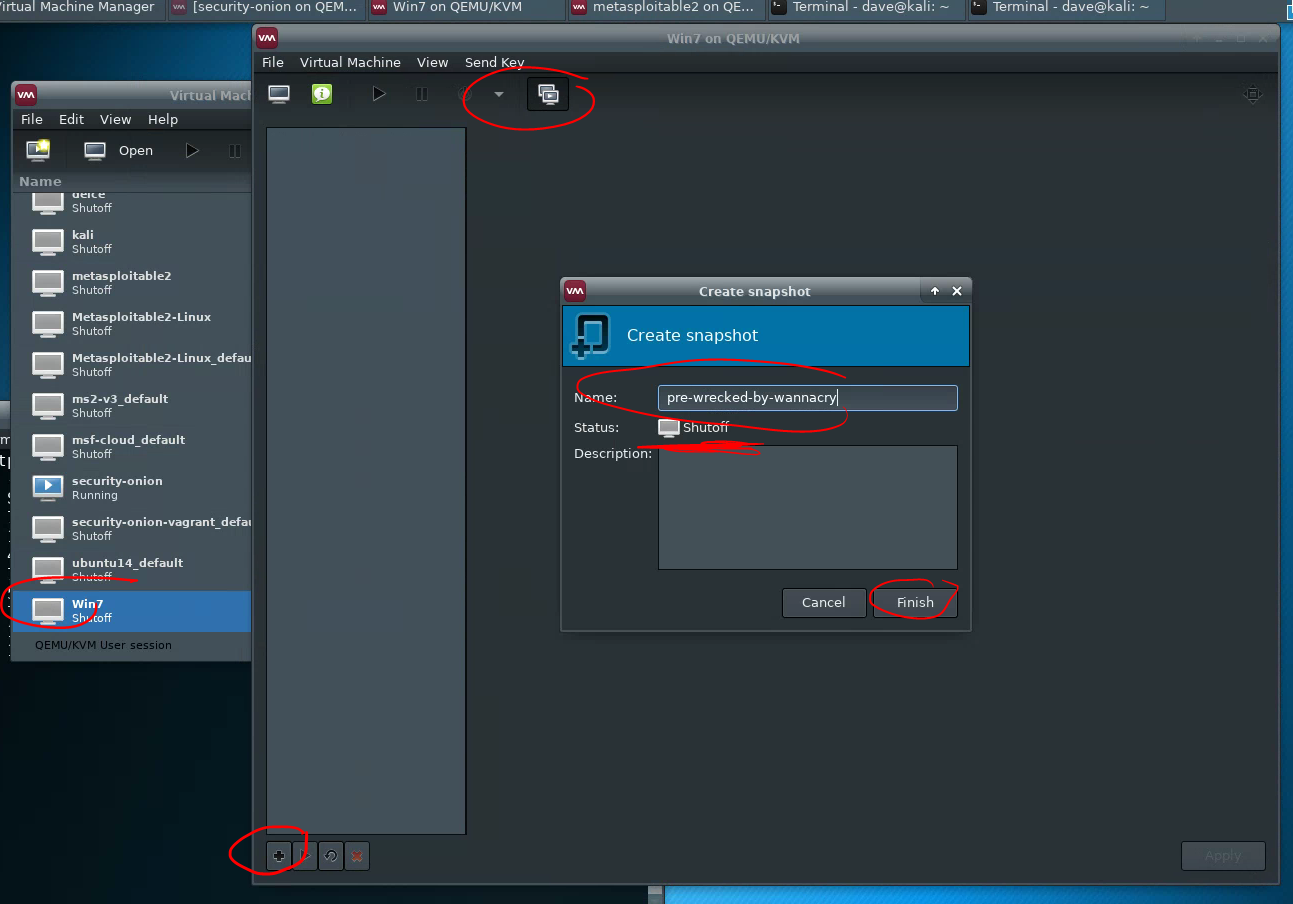
To create a snapshot, first, shut down the virtual machine. Then, click the “snapshot” button on the virtual machine pane, then +, then set a name, and “Finish.”
Restoring a snapshot
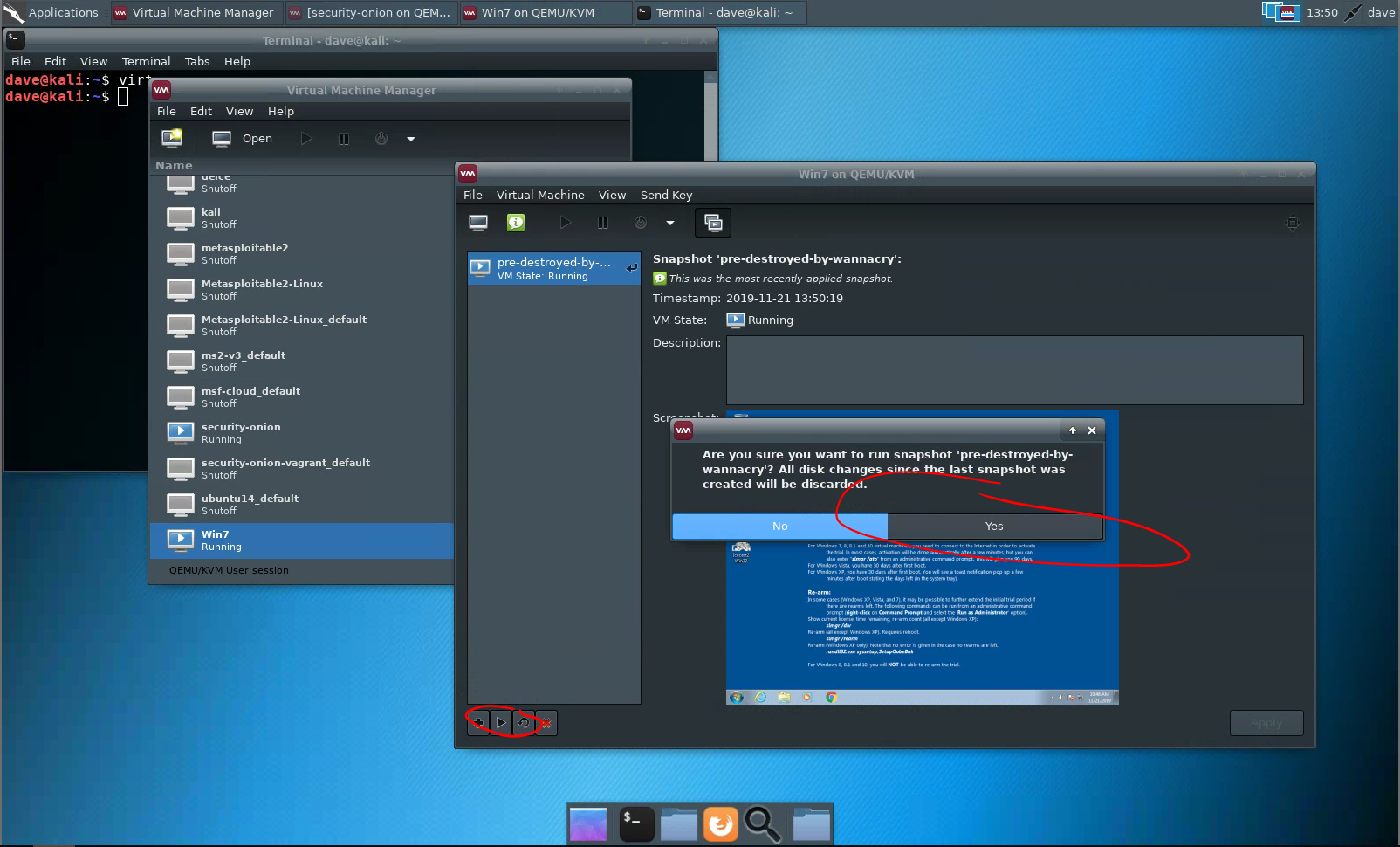
To restore to a snapshot, select your snapshot, and then “play” it. You do not need to shut down the virtual machine before restoring a snapshot.
How I created the virtual machines
If you are curious how the lab was set up, then browse this github repository.